Secret Blizzard, a sophisticated Russian nation-state threat actor Known for its stealthy espionage operations has just launched a custom malware named ApolloShadow.
The threat actor (also known as Turla, Snake, Uroburos, Waterbug, Venomous Bear and KRYPTON) uses an adversary-in-the-middle (AiTM) attack method at the ISP level to deploy the malware.
Shadowing the Malware
The malware first installs a fake Kaspersky Anti-Virus certificate, making your devices trust harmful websites.
This gives attackers long-term access for spying and stealing your login details.
Once it's on your system, ApolloShadow tries to gain more control by weakening network settings, creating a hidden admin account, and installing certificates that hide browser security warnings.
This is the first strong evidence that Secret Blizzard can carry out attacks at the ISPlevel.
How Apollo Works
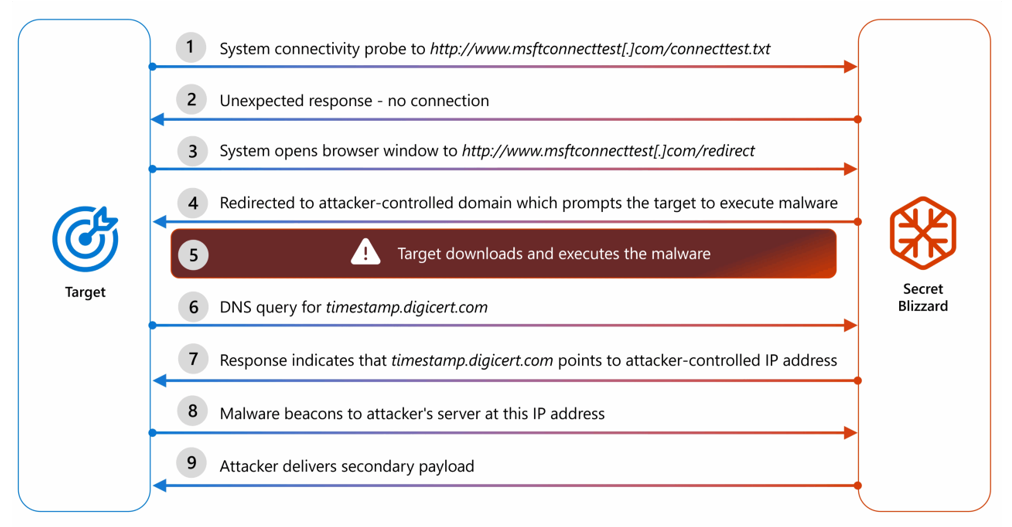
Initial Access: Victims are redirected through a fake captive portal (legitimate web pages designed to manage network access) via ISP-level access. They are tricked into downloading a fake Kaspersky installer that delivers ApolloShadow.
Execution & Privilege Escalation: ApolloShadow checks for admin rights. If not granted, it prompts the user to approve elevated access, pretending to be Kaspersky. Depending on the access level, it performs limited or full system modifications.
Communication & Payload Delivery: The malware sends disguised system data to trusted-looking domains using DNS manipulation. If the server responds correctly, it downloads and runs additional malicious scripts.
Persistence & Certificates: Installs rogue root certificates to make malicious sites appear trusted while also adjusting Firefox settings to accept these certificates.
System Reconfiguration: Changes network profiles to "Private" and enables sharing features, reducing network security.
Backdoor Creation: Creates a hidden local admin account with a fixed password for long-term access.
Evasion Tactics: Uses simple encryption to hide key code and delays certain changes until reboot for stealth.
The ApolloShadow malware adapts its execution based on privilege level. When privileges are low, it collects host IP data, encodes it, and sends it via a fake Digicert domain to its command-and-control server. While elevated privileges make system-level changes, it sets networks to private to weaken firewall protections, enables file sharing, installs rogue root certificates and adds a hidden admin user with a hardcoded, non-expiring password maintain long-term control over the device.
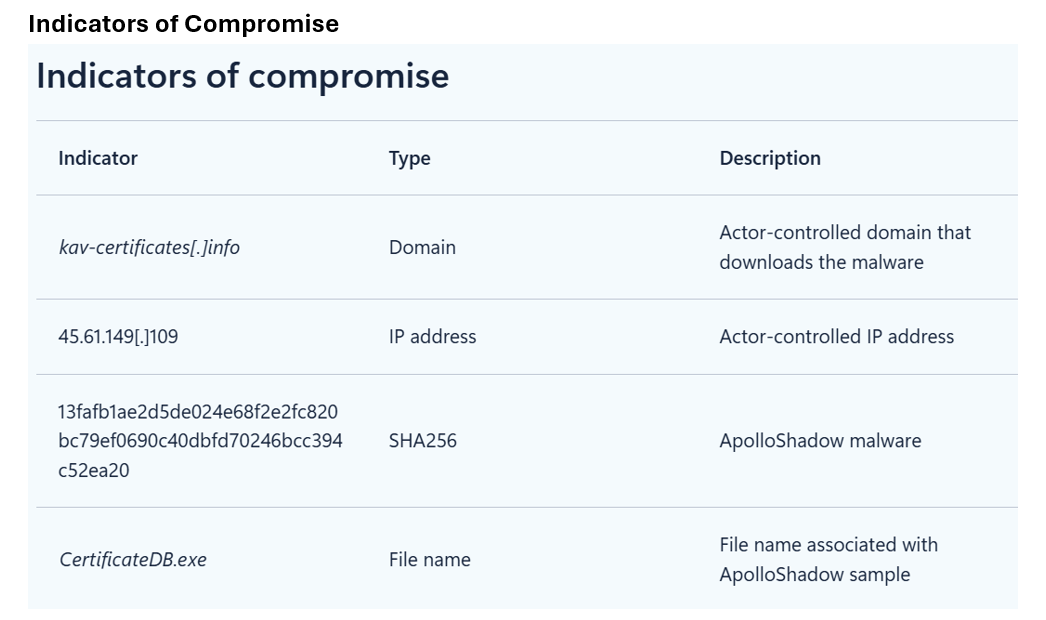
Defense Against the Blizzard
· Apply the Principle of Least Privilege by ensuring users have only the minimum access necessary to perform their tasks.
· Enable Multifactor Authentication (MFA) and audit privileged account activity to detect and disrupt attacker movement.
· Regularly review membership of highly privileged groups such as Administrators, Remote Desktop Users, and Enterprise Admins.
· Enable cloud-delivered protection in Microsoft Defender Antivirus or your preferred antivirus solution to stay ahead of rapidly evolving threats.
· Use attack surface reduction (ASR) rules to block common attack techniques at the endpoint.
· Restrict executable file execution based on factors like prevalence, file age, or trusted sources.
· Prevent execution of potentially obfuscated scripts to reduce script-based attack vectors.
By implementing these measures proactively, you strengthen your organization's security posture, reduce attack surface, and make it significantly harder for adversaries to succeed.








.png)
.png)