They say curiosity kills the cat, but in cybersecurity, it’s the “click” that kills the system.
We’ve all done it. That one rushed momentwhere you skip over the download source check, ignore the file name, and click "Next" five times without reading. After all, it’s just a browser update, right?
Well, buckle up. Because that innocent installer could very well be part of a stealthy, memory-resident malware campaign that’s quietly setting up shop right inside your machine. And this time, it’s not just any malware, it’s the Catena chain, and it’s purring maliciously from your memory.
When Your Favorite Apps Come with Uninvited Guests
Since February 2025, there has been tracking of a sly operation that’s wrapping trojans in the skin of legitimate software installers from QQBrowser to LetsVPN to Google Chrome clones.
These aren’t your typical shady downloads. They're beautifully signed, visually identical to the real thing.
At the heart of this campaign lies a modular loader called Catena, a multi-stage trap that, like a Russian nesting doll of doom, unpacks layer after layer of malicious logic without ever writing to disk.
What Makes Catena So Dangerous?
Well, maybe the fact that the attack unfolds like this:
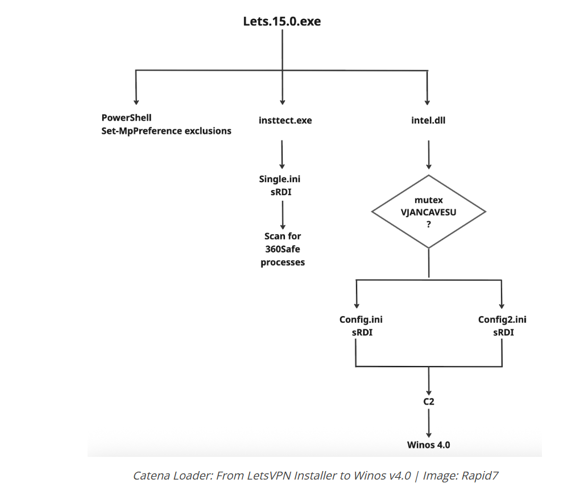
Trojanized Installer Launch:
The user runs what appears to be a legit app setup (QQBrowser_Setup_x64.exe), kicking off the chain.
Stage 1 – The Decoy Drop:
It installs a real app (decoy), while quietly dropping hidden files like insttect.exeand .ini scripts and disables Microsoft Defender. Smooth.
Stage 2 – The Real Payload:
Now it injects malicious DLLs (e.g., intel.dll) into memory using Shellcode Reflective DLL Injection (sRDI) never touching disk, leaving almost notrace.
Persistence Layer:
- Scheduled tasks using PowerShell
- monitor.bat watchdog scripts
- Mutex switching logic to rotate payloads
Expired legitimate certificates + signed decoy apps for social engineering flair
And then comes the kicker.
The Winos v4.0 RAT Deployment
A memory-only remote access tool packed with:
- C2 beacons
- IP resolution via getaddrinfo
Runtime logic that can execute next-stage payloads directly in memory
Even scarier? The entire tool kit fits in just 112KB, which is lighter than most memes you’ll find on WhatsApp.
Who’s the Target?
☑️ Confirmed IPs
- 103.46.185[.]44
- 112.213.101[.]139
- 47.238.125[.]85
- 137.220.229[.]34
- 202.79.171[.]133
All signs point toward regional espionage or financial reconnaissance, likely tied to Silver FoxAPT.
How to Defang the Catena Chain
Harden Endpoint Detection
- Use EDR tools with reflective injection detection (e.g., CrowdStrike, SentinelOne).
- Enable Memory Scanning for unsigned DLLs.
- Monitor regsvr32.exe, powershell.exe, and schtasks.exe for unusual invocations
- Block Known Indicators
- Create YARA rules to flag known Catena behaviors.
- Block outbound connections to known C2 IPs and ports used by Winos.
- Prevent execution of *.ini-based loaders in %APPDATA% paths.
Application Control + User Awareness
- Implement Application Whitelisting via Windows Defender App Control (WDAC).
- Alert users to avoid downloading software from unofficial sources — even if it “looks” legit.
- Roll out internal newsletters showing side-by-side comparisons of decoy vs. authentic installers.
Threat Hunting
- Look for these red flags in telemetry:
- Unusual regsvr32 executions
- Scheduled tasks named Policy Management
- App installations followed by Defender tampering
Hunt for CreateMutexA logs or any unusual behavior tied to mutex naming patterns.
Catena is a reminder that the threat isn’t always on the hard drive, it’s often living in the shadows of your RAM.
This campaign blends deception, stealth and persistence so well, it could win an Oscar. But it’s not a movie. It’s happening in real time.
As history shows us, today’s regional threat is tomorrow’s global breach.
Stay alert. Trust nothing. Monitor everything!!!!!!!!








.png)
.png)