Skeleton Spider(FIN6) is once again demonstrating how social engineering and cloud infrastructure can be blended into a convincing and lethal cocktail. Shifting from their classic point-of-sale heists to full-fledged enterprise targeting, this crew now uses fake job applicants, cloud-hosted resumes, and CAPTCHA gates to sling malware past your defenses.
Their campaign, centered around the More_eggs backdoor, is deceptively simple but highly evasive just a ZIP, a shortcut, and a cloud… and suddenly, your network has guests it never invited.
Recruiters Beware: That Perfect Resume Might Be a Trap
Skeleton Spider starts with trust, more specifically, your trust.
- The threat actors reach out via LinkedIn or Indeed, posing as skilled professionals looking for opportunities.
- After building rapport, they follow up with a message like:
“Hi, please find my resume at bobbyweisman[.]com – I look forward to hearing from you!”
No links, no red flags… at first glance.
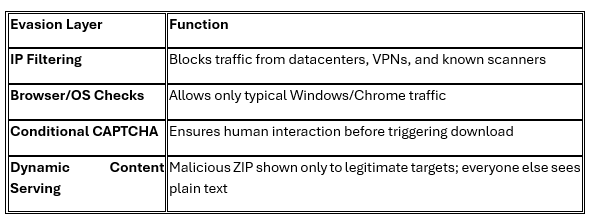
- The resume site is hosted on AWS infrastructure, designed to resemble a personal portfolio complete with CAPTCHA and a professional-looking interface.
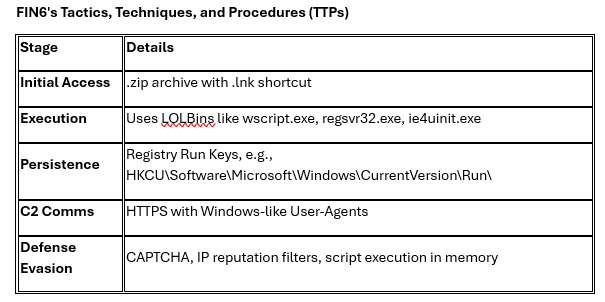
· Clicking the download link triggers a ZIP file containing a .LNK file (Windows shortcut) disguised as a document. Once executed, this shortcut silently runs JavaScript viawscript.exe, dropping the More_eggs malware.
Why the Cloud Makes It Worse
FIN6 has figured out how to abuse the cloud’s strengths to hide in plain sight.
They use AWS services like:
- Amazon CloudFront to hide their server origins
- S3 buckets and EC2 instances for hosting
- CAPTCHA gates + fingerprinting to limit exposure to only intended victims
- Disposable cloud infrastructure that’s easy to spin up, hard to track
These cloud-hosted resume pages come with impressive evasion features:
Inside the Egg: The Malware Chain
Once downloaded and executed, the ZIP contains:
- A .LNK shortcut, disguised as a DOC or PDF
- The LNK silently runs JavaScript via wscript.exe
- Downloads and executes More_eggs – a modular backdoor
What More_eggs can do:
- Inject commands remotely
- Steal credentials
- Drop follow-on payloads (including ransomware)
- Remain memory-resident for stealth
- Call home via HTTPS with spoofed headers
FIN6'sTactics, Techniques, and Procedures (TTPs)
How to Defend Yourself and Your Organization
For HR and Recruiting Teams:
- Avoid typing URLs from unsolicited messages always verify independently.
- Report suspicious resume domains to your IT/security team immediately.
- Don’t trust CAPTCHA alone CAPTCHA-protected doesn’t mean legit.
For Security Teams:
- Block .LNK execution from untrusted ZIP sources
- Monitor use of LOLBins, especially when launching PowerShell or JavaScript
- Detect base64-encoded PowerShell scripts
- Monitor outbound traffic to new, suspiciously named domains (firstlast[.]com format)
- Track domain WHOIS changes recently re-registered domains could signal reuse
- Implement strict controls on AWS and similar cloud access from unknown entities








.png)
.png)