When a wolf changes its fur, it doesn't mean it's given up on the hunt.
There’s a new ransomware-as-a-service (RaaS) player in town called Chaos, and while the name might ring a familiar bell, let’s not get it twisted, this isn’t a remix of the old Chaos malware.
Old Gang, New Branding
It’s like a reboot nobody asked for but somehow, it’s more dangerous. And this isn’t your average copy-paste threat group.
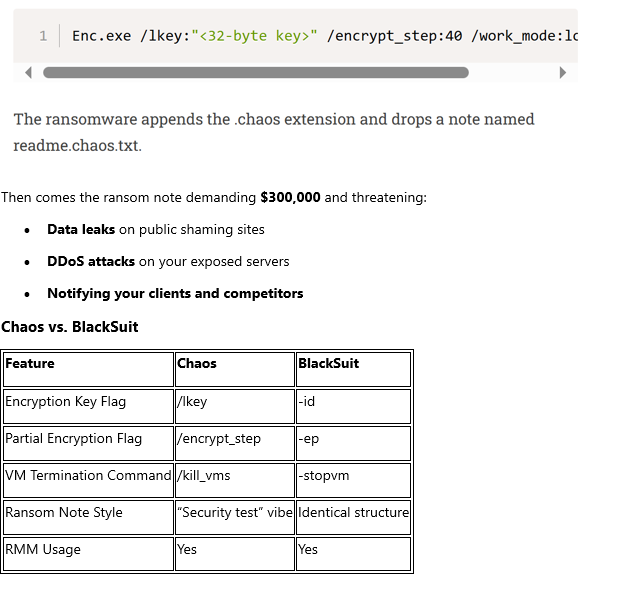
Evidence suggests Chaos might be the evolution of Black Suit:
- Similar ransom note tone (This was just a security test. Pinky promise. Pay us.”)
- Identical encryption commands
- Nearly matching toolkits and behaviors
So don’t be fooled by the name change. Thehouse may look different, but the burglars haven’t switched careers.
Vishing Is the New Phishing
While other ransomware gangs are stillsliding into inboxes, Chaos is making phone calls.
Here’s how they play their game:
· Targets get spammed withfake IT alerts.
· They're urged to call afake “tech support” hotline.
· Once on the line, victimsare manipulated into launching Microsoft Quick Assist, essentiallyopening the front door and inviting the attacker in for coffee.
Smooth, right?
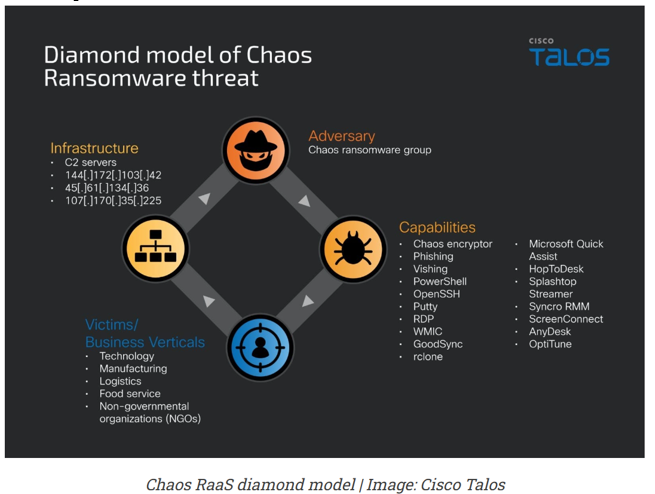
Once inside, Chaos actors install a buffetof Remote Monitoring and Management (RMM) tools like:
- AnyDesk
- ScreenConnect
- OptiTune
- Syncro RMM
- Splashtop
Why? Persistence. Control. Comfort.
Recon,Ransom, Repeat
- Reconnaissance: They run tools like ipconfig, tasklist.exe, and nltest to map the network like it’s a vacation rental.
- Credential Harvesting: Fancy techniques like Kerbe roasting, and classic password resets via net.exe.
- Stealthy Persistence: Registry tweaks hide user accounts, and MFA apps are disabled using wmic. You didn’t even know you had guests, did you?
And when they’re ready to drop the hammer?
They run:
bash
CopyEdit
Enc.exe /lkey:"<32-bytekey>" /encrypt_step:40 /work_mode:local_network
Translation: Encrypt everything.Fast, quiet, and lethal.
Files get slapped with a .chaos extension,and a ransom note (readme.chaos.txt) lands on your screen, sweetly calling thisan “IT audit.”
Encryption, Evasion & Extortion
Chaos ransomware uses:
- Elliptic Curve Diffie-Hellman (ECDH) + AES-256 encryption
- Multi-threading for rapid file encryption
- Selective targeting to avoid system-breaking mistakes
And they’re slippery:
- Avoiding sandboxes and VMs
- Obfuscating strings
- XOR-encrypting their config and ransom notes
Basically: they came prepared. They’re nothere to make rookie mistakes or trigger early alarms.
Double Extortion and DDoS Drama
Encrypting your files is just Act 1.
Act 2? Stealing your data.
They use the legit GoodSync backuptool renamed to wininit.exe to exfiltrate files to cloud storage. Large files and uncommon types are filtered out to fly under your security radar.
Whether they call themselves Chaos, BlackSuit, or something shinier next quarter, it’s clear these attackers are leveling up their branding, playbooks, and emotional manipulation.
The attacks are smoother, the storytelling is cleaner, and the stakes. Higher than ever!!!
Remember, every unlocked door is an invitation.
What You Can (and Should) Do Now
Disable Microsoft Quick Assist organization-wide
Block installations of AnyDesk, ScreenConnect, Splashtop, and the likes
Train your employees to spot vishing tactic,especially the “urgent call IT now” messages
Harden your endpoints with EDR/XDR and set traps for suspicious behaviors
Inspect cloud backups
Segment your network, lock down lateral movement, and audit service accounts regularly.








.png)
.png)