The Oystermalware, a backdoor malware that was first seen in July 2023 has beenlinked to the Russian linked threat group ITG23 also known as Periwinkle Tempest, Wizard Spider or Gold Blackburn.
The malware also known as Broomstick or Cleanup Loader, tricks users into downloading malicious installers, potentially paving the way for ransomware infections like Rhysida.
How It Works
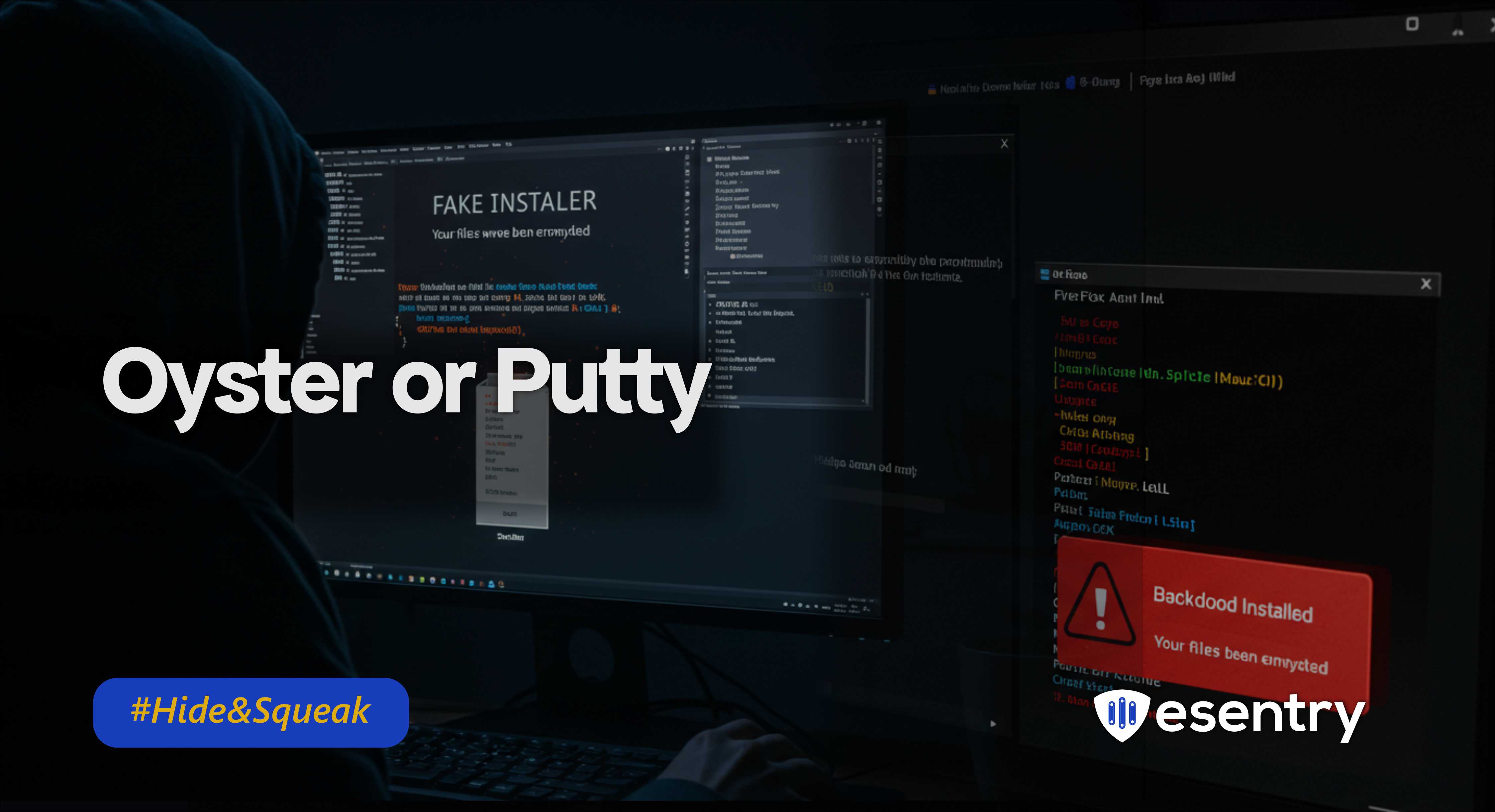
Deceptive Search Results: Threat actors use SEO poisoning to push fake software download sites (e.g.,updaterputty[.]com) to the top of search results for popular tools like PuTTY.
Malicious Download: Users are lured to fake sites, causing them to download what appears to be alegitimate installer (e.g., PuTTY-setup.exe), which is malicious.
Backdoor Installation: Executing the fake installer drops and runs a malicious DLL (zqin.dll), establishing the "Oyster backdoor" on the system.
Data Theft & Control: The Oyster backdoor immediately begins stealing system information and credentials and can execute further commands or download additional malware.
Persistence Achieved: The malware ensures it remains active by creating a recurring scheduled task knownas FireFox Agent INC
Impact
Network Compromise Risk: A single click on a poisoned search result can lead to the compromise of entire networks. For IT administrators, the danger is critical.
Confirmed Malicious Activity: Sandbox analysis verified the file's malicious behavior, confirming theexecution of a malicious DLL and the creation of a persistent scheduled task.
High Potential for Data Theft: The malware's capabilities including credential stealing means the potential for significant data theft remains high.
HighPotential for Ransomware: Similarly, the backdoor's ability to download additional malware poses a substantial risk of ransomware infections.
Revoked Certificate Use:The fake installer uses a revoked digital certificate, a tell-tale sign of malicious activity and a link to other ongoing attack campaigns.


Recommendations and Mitigations
User Education: Educate users on the critical importance of verifying download sources and being wary of unexpected installers.
Multi-FactorAuthentication (MFA): Enable MFA across all possible accounts and systems to add a crucial layer of security, even if credentials are stolen.
Endpoint Detection Tools: Deploy robust Endpoint Detection and Response (EDR) solutions to identify and respond to malicious activity on user work stations.
Proactive Threat Hunting: Regularly hunt for suspicious scheduled tasks within the IT environment, as these are often used for persistence by malware.
Certificate Monitoring: Implement monitoring for the use of revoked digital certificates, which can bea strong indicator of malicious software.
Vigilance Against SEO Poisoning: Maintain high vigilance against deceptive SEO poisoning tactics, understanding that attackers are actively manipulating search results to deliver malware.
This Oyster attack is just a clear sign that keeping our digital stuff safe isn't just the job of IT pros. It's about all of us staying sharp, being smart about what we click, and knowing that a little bit of vigilance goes a long way. Ultimately, protecting our information and keeping everyone's trust strong, that's what really counts.







.png)
.png)