The SmartApeSG threat actor is conducting an active campaign leveraging compromised websites to deploy sophisticated "ClickFix" social engineering attacks. This operation bypasses traditional security controls by weaponizing user trust and manual execution, resulting in NetSupportRAT and StealC v2 infections across multiple sectors.
Primary Vectors: Compromised websites, clipboard manipulation
Target Sectors: Multi-sector campaign affecting various industries
Payloads: NetSupport RAT, StealC v2 information stealer
ATTACK METHODOLOGY
Initial Compromise
SmartApeSG compromises legitimate websites and injects malicious JavaScript to create convincing fake CAPTCHA overlays that mimic genuine verification systems.
User Manipulation
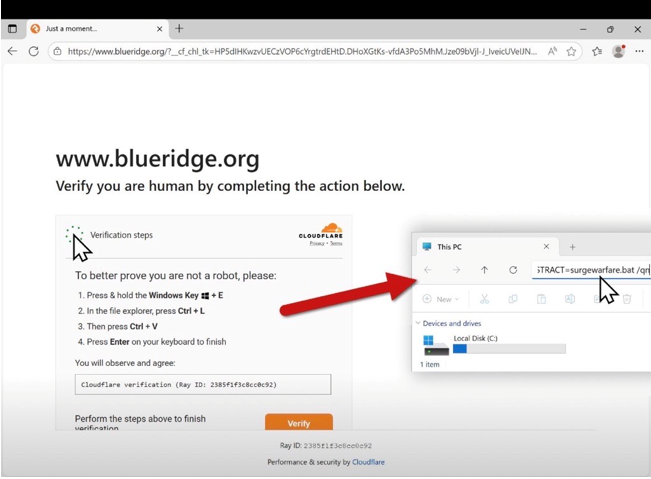
Victims encounter what appears to be a standard "I'm not a robot" verification prompt. However, the fake CAPTCHA instructs users to:
- Press Win + R to "verify" their identity
- Paste clipboard contents into the Windows Run dialog
- Execute the command by pressing Enter
Clipboard Weaponization
When users click the fake CAPTCHA button, malicious PowerShell commands are silently copied to their clipboard through a technique known as "paste jacking." Users unknowingly paste and execute these commands, believing they're completing a legitimate verification.
Payload Deployment
The executed PowerShell script initiates a download chain that delivers:
- NetSupport RAT: Provides persistent remote access and command execution
- StealC v2: Harvests credentials, browser data, and sensitive information
TECHNICAL INDICATORS
Attack Characteristics:
- Exploitation of user trust rather than technical vulnerabilities
- Manual execution bypasses automated security controls
- Uses legitimate system tools (PowerShell, Run dialog) for malicious purposes
- Multi-stage payload delivery obscures initial detection
Related Techniques:
- File Fix Variant: Similar campaign using file upload manipulation and steganographic image concealment .
- Both variants represent evolution of command-injection social engineering.
ATTRIBUTION
While SmartApeSG's ultimate objectives remain under investigation, the dual-payload approach (remote access + data theft) suggests either:
- Initial access broker operations for ransomware affiliates.
- Direct financial motivation through credential monetization.
- Espionage activities targeting specific sectors.
DEFENSIVE RECOMMENDATIONS
- Hunt for IOCs: Search for NetSupport RAT and StealC v2 signatures in your environment.
- Review PowerShell logs: Analyze command-line activity for suspicious execution patterns.
- User notification: Alert staff about fake CAPTCHA campaigns via security awareness channels.
- EDR tuning: Configure endpoint detection rules for anomalous PowerShell execution and clipboard manipulation.
- Network monitoring: Implement blocking for known C2 infrastructure associated with NetSupport RAT.
- Group Policy restrictions: Consider disabling Windows Run dialog (Win + R) for non-administrative users.
- Application allow listing: Deploy comprehensive whitelisting to prevent unauthorized executable launches.
- User training enhancement: Integrate ClickFix/FileFix scenarios into security awareness programs.
- Web filtering: Strengthen URL reputation services and content inspection capabilities.







.png)
.png)