SolarWinds Web Help Desk (WHD), a tool designed to support IT operations, is being misused and repurposed into a dangerous entry point, effectively transformed from a support system into a launchpad for invisible shadow servers.
Rather than carrying out quick break-ins to steal data and disappear, this activity focuses on quiet, long-term presence. By exploiting security weaknesses in exposed or unpatched WHD systems, unauthorized access is gained and used to silently deploy virtual computers within an organization’s network. These hidden environments can operate unnoticed for a long period .
The threat is serious because attackers use QEMU virtual machines, a type of software that lets them run hidden, separate computers inside a single real server.
Key Concepts Explained
- SolarWinds WHD: This is software used by organizations to manage IT support requests. It helps IT teams track and resolve issues efficiently.
- QEMU: An open-source machine emulator and virtualizer that allows users to run multiple operating systems on a single physical machine. Attackers can use QEMU to create virtual environments that mimic real systems.
- Virtual Machines (VMs): These are software-based simulations of physical computers. They allow multiple operating systems to run on a single hardware platform, making them useful for testing, development, and running applications in isolation
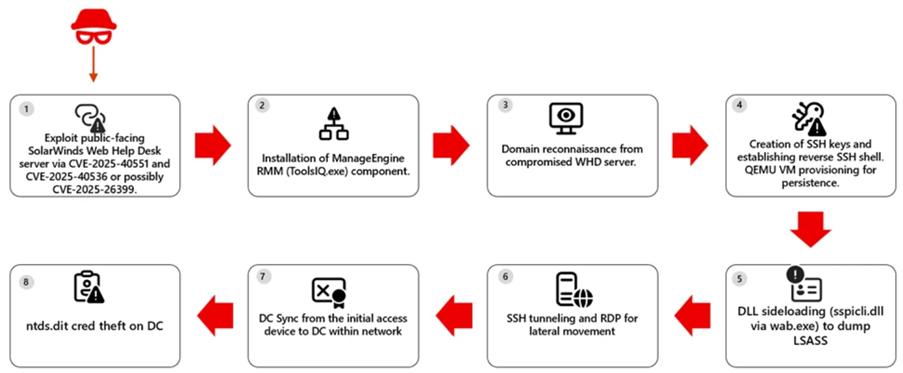
How the Exploit Works
- Initial Access via Unpatched WHD: WHD systems that were exposed to the internet and vulnerable due to missing security updates. They exploited one or more weaknesses that allow remote attackers even without a login to run commands on the server. This type of weakness is known as Remote Code Execution (RCE).
- Stealthy Download of Tools: After taking control of the WHD application, the hackers used built-in Windows tools (like PowerShell) to quietly download additional software including remote management tools that let them stay connected and control the system from afar.
- Hidden Virtual Machines (QEMU): Instead of just dropping malware, a virtual machine is created .The VM is launched automatically every time the machine reboots. Because the malicious activity ran inside this VM, it might be undetectable by traditional security tools.
- Hidden Remote Access: The virtual machine was set up to allow remote access through an encrypted connection (SSH) using a forwarded network port. In simple terms, this created a secret backdoor that lets attackers move quietly, bypassing normal security checks while staying hidden inside what looks like a legitimate virtual machine.
- Credential Theft and Lateral Movement: To expand their control, a technique called DLL side-loading is use to trick a trusted system program into loading a malicious library. This allowed them to extract administrator credentials
Why This Matters
What makes this campaign serious is how the attackers:
- Bypassed normal protections without needing valid credentials
- Hid in plain sight using virtual machines (QEMU)
- Use legitimate administrative software for persistence
- Use Stolen credentials to expand control across a compromised network
Recommendations
- Apply the Latest Patches: Ensure WHD is updated to version 2026.1 or newer, older versions are known to be exploitable.
- Remove Public Internet Access: Do not expose WHD admin portals directly to the internet. Use VPNs, firewalls, or private networks instead.
- Check for Hidden Virtual Machines: Look for unexpected scheduled tasks that launch virtual environments (e.g., QEMU VM) especially ones set to run at system startup.
- Audit for Unauthorized Tools: Search for unauthorized RMM or remote access tools installed .
- Review High-Privilege Credentials: passwords for admin and service accounts especially ones reachable via WHD should be reset .
- Isolate Suspicious Hosts: If a machine is suspected of compromise, isolate it from the network and perform a full forensic review.
This incident is a reminder that unpatched, internet-facing applications are extremely risky. One overlooked vulnerability can give attackers a foothold, allowing them to take over an entire networks while staying hidden by implementing advanced evasion technique







.png)
.png)