A recent wave of cyberattackshas been targeting SonicWall SSL VPN devices, with threat actorsdeploying Akira ransomware in a wave of activity that began in late July2025.
Thecampaign which remains active, with new infrastructure linked to it hasbeen recently observed as of September 20, 2025. Attackers were able to access SonicWallSSL VPN accounts using credentials likely obtained through CVE-2024-40766,even bypassing OTP-based MFA.
In recent cases, threat actors have progressed from credential access to lateral movement, data theft, and encryption in under 4hours with the fastest observed intrusion taking only 55 minutes.
SonicWall Intrusion Analysis
Initial Compromise
· Threat actors gain entry through stolen credentials on SonicWall SSL VPN infrastructure.
· Multi-factor authentication controlsare bypassed.
Reconnaissanceand Horizontal Movement
· Rapid network enumeration occurswithin minutes of successful authentication.
· Common target services include SMB(port 445), RPC (port 135), and SQL Server (port 1433).
· Reconnaissance toolsets includeImpacket framework, SoftPerfect Network Scanner, and Advanced IP Scanner.
ElevatedAccess and Foothold Establishment
· New administrative accounts areprovisioned.
· Existing account privileges areelevated.
· Remote access solutions such as AnyDesk,TeamViewer, RustDesk are deployed for persistent access.
· Alternative persistence mechanismsinclude SSH reverse tunnels and Cloudflare Tunnel infrastructure.
Security Control Subversion
· Attempts to neutralize endpoint protection such as Windows Defender and EDR.
· Employed a bring your own vulnerable driver (BYOVD) technique to tamper with security software at the kernel level.
· Volume Shadow Copy deletion to blockrecovery capabilities.
RansomwareDeployment
· Akira ransomware is deployed as thefinal payload.
· Common executable names observed: akira.exeor locker.exe.
· Encryption targets include network-attached storage and shared drives.
· Ransom demands are issued following successful encryption.
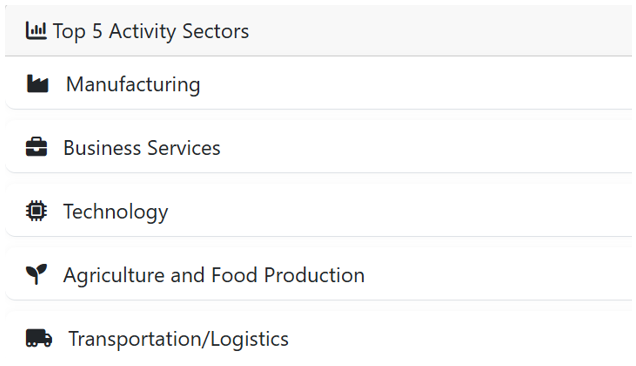
Sectors Affected: Below isa list of top sectors targeted
Defensive Measures
Organizations should monitor for
· Unusual archive creation activity(especially large WinRAR operations)
· Unexpected use of file transfertools like rclone or FileZilla
· Outbound data transfer anomalies
· Suspicious executables matchingknown ransomware naming conventions
Recommendations
SonicWallhas confirmed active exploitation of CVE-2024-40766 in observed attackcampaigns. What this means is that
· Organizations that have appliedpatches may remain at risk
· Compromised credentials obtainedprior to patching can still provide attacker access
· Patching alone does not remediatepre-existing credential theft
Recommendedactions include:
· Reset all VPN user credentials, even on patched systems
· Review authentication logs for suspicious access patterns preceding the patch deployment
· Consider mandatory password resets for all VPN users
· Enable additional authentication controls beyond basic credentials
· Monitor for unauthorized access attempts using previously valid credentials
Stay safe!








.png)
.png)