Proverbially speaking, not all that glitters is gold, and not every browser window leads to safety. In today’s cyberspace, even a click can become a keyhole through which your entire digital life is quietly observed, harvested, and exfiltrated. And sometimes, the thief doesn’t even wear a mask, it’s dressed in Rust.
If you’ve never heard of RustStealer, allow us to make the introduction.
It’s new. It’s quiet. It’s slick. And it wants everything you’ve typed into your Chromium browser.
The Languageof Attackers Evolves
In the wild world of malwares and ransomwares, Rust is the new kid with sharp teeth. It’s a language beloved by developers for its performance, memory safety, and sleekdesign. But recently, attackers have discovered it too, and that’s how RustStealer was born.
This isn’t just a lazy key logger or a recycled Trojan. This is a well-coded, memory-safe,security-aware info-stealer built from scratch to slip through cracksand pry open your browser’s vaults.
That means your passwords, session cookies, browsing history, and even your crypto wallet plugins are all up for grabs.
And just to addsome spice? It's modular. It can evolve mid-operation.
Threat actors can push updates remotely, so what’s just a stealer today could become ransomware tomorrow.

Phishing Hooks and Browser Crooks
RustStealer doesn’t walk through the front door. It’s a phishing game, cloaked in emails that look just legit enough to slip past your skepticism. The payload? A malicious attachment or a poisoned link.
Once clicked, it lands quietly, and from there:
- It digs into your browser profile, focusing on Chromium-based apps like Chrome, Edge, Brave, and Opera.
- It extracts login credentials, session tokens, cookies, and more.
- It even hunts down cryptocurrency wallets tied to browser extensions.
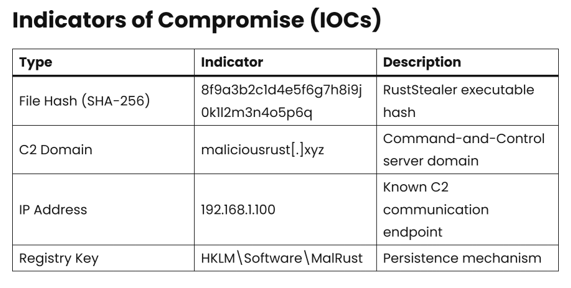
What makes it particularly nasty is its use of encrypted comms and obfuscation, which means the data it sends home, often to remote command-and-control (C2) servers,doesn’t raise easy red flags. Your firewall barely flinches.
Shape-Shifter
Think of RustStealer as a cyber toolkit, not just a tool.
Its modular architecture means it can be remotely updated, extended, and repurposed for deeper infiltration. Tomorrow, it might record your keystrokes. Next week, it could drop a ransomware payload. And the worst part? Its Rust foundation make sit painstaking to reverse-engineer. Traditional antivirus tools just don’t recognize what they don’t understand.

It’s malware...built like a startup.
The arrival of Rust Stealer is more than another line in the CVE database, it’s a marker inthe cyber timeline.
It tells us that malware authors are upgrading, getting smarter, and treating their campaigns like mature software projects.
And while that sounds bleak, it also reminds us: we must evolve too.
What Can You Do?
Strengthen Phishing Defenses
Use sand boxing tools, mail filters, and educate your staff. Most infections still start with one bad email.
Deploy EDR with Behavioral Analytics
RustStealer isn’t noisy, but EDR tools that use behavioral detection (not just static signatures) have a better chance of catching its shady activity.
Isolate and Protect Browser Profiles
Don’t store sensitive credentials in your browser, use password managers that encrypt and protect your information.
Watch for Registry and Scheduled Task Modifications
RustStealer uses these to persist post-reboot. Periodic registry audits and system monitoring tools can help surface anomalies.
Protect Crypto Wallet Extensions
Treat them like bank accounts. Use hardware wallets for larger holdings and disable browser plugins when not in use.
Monitor Network Traffic for Encrypted Exfiltration
Configure your SIEM to alert on strange outbound traffic, even if it’s encrypted. Look for patterns, not content.
The battle has moved into your browsers!!!!
With the right mindset, and just a touch of paranoia—we can outsmart even Rust.








.png)
.png)