If you thought the chaos of Lapsus$ and its copycats was history, think again. A new collective calling itself Scattered Lapsus$ Hunters has resurfaced and this time, they’ve set their sights on Salesforce. The group popped up recently with a shiny new leak site, claiming to have 1 billion Salesforce records ready to spill unless their extortion demands are met. True to the Lapsus$ legacy, they’re loud, theatrical, and eager to prove they’re back in business.
If the name “Lapsus$” rings a bell, it should because the original gang caused global headaches in 2022, breaching Microsoft, Okta, Uber, and others often using the same mix of SIM swapping, vishing, and insider manipulation.
“Scattered Lapsus$ Hunters” appears to be reviving that legacy, mixing tactics from groups like Scattered Spider and Shiny Hunters hence the mashup name.
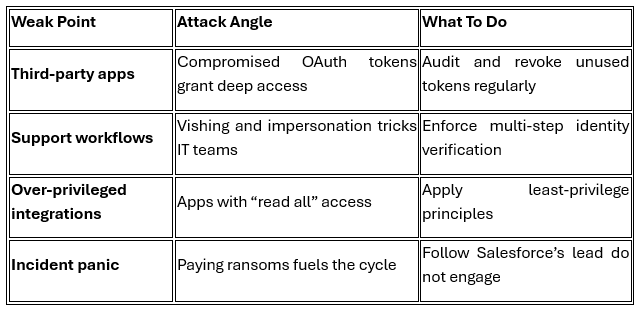
According to reports, the actors are blending old-school social engineering with a dash of OAuth token abuse to breach corporate systems. Think “vishing”(voice phishing) meets “API hijacking.” Instead of smashing through firewalls, they’re charming their way in impersonating vendors, IT support, or third-party partners to gain access. Once inside, they reportedly exploit connected apps and OAuth tokens, turning convenience into compromise.
Interestingly, Google’s Threat Intelligence Group had already spotted the storm brewing.
Back in August, they warned Salesforce customers of a “credible theft campaign” targeting customer data, specifically via third-party integrations.
So, while this breach is making headlines now, the signals were already on the radar another reminder that threat intelligence isn’t just a buzzword; it is a weather forecast for cyber risk.
Salesforce Responds
Salesforce has confirmed that its core platform remains secure, with no evidence of a direct breach. The reported data exposure stems from a compromised third-party integration, specifically the SalesLoft Drift app, which became the weak link in the chain. According to Bloomberg, the extortion group Shiny Hunters has claimed responsibility, alleging they stole data from roughly 40 Sales force clients; a haul they say includes 1 billion records. Salesforce is investigating the incident, emphasizing that the breach involved external integrations and stolen credentials, not the company’s own systems.
Lessons From the Breach
This incident underlines an uncomfortable truth: your SaaS security is only as strong as your integrations.
The more connected your tools are, the wider your attack surface becomes.
What Security Teams Should Do (Right Now)
- Audit your OAuth tokens. Identify which apps are connected to Salesforce and revoke any that aren’t essential.
- Tighten support processes. Enforce identity verification for anyone requesting password resets or access changes even if they sound legit.
- Turn on MFA everywhere. Especially for Salesforce admins, third-party connectors, and service accounts.
- Monitor for strange behavior. Sudden data exports, permission escalations, or new token grants could be red flags.
- Educate your staff. Vishing and impersonation aren’t just “phishing with a phone” they’re human-driven breaches in disguise.



.jpeg)
.jpeg)
.jpeg)


.png)
.png)