Platforms Affected: iOS, macOS, iPadOS
Exploited Component: WhatsApp messager
A zero-click remote code execution (RCE)vulnerability in WhatsApp, affecting Apple’s iOS, macOS, and iPadOS platforms has been discovered.
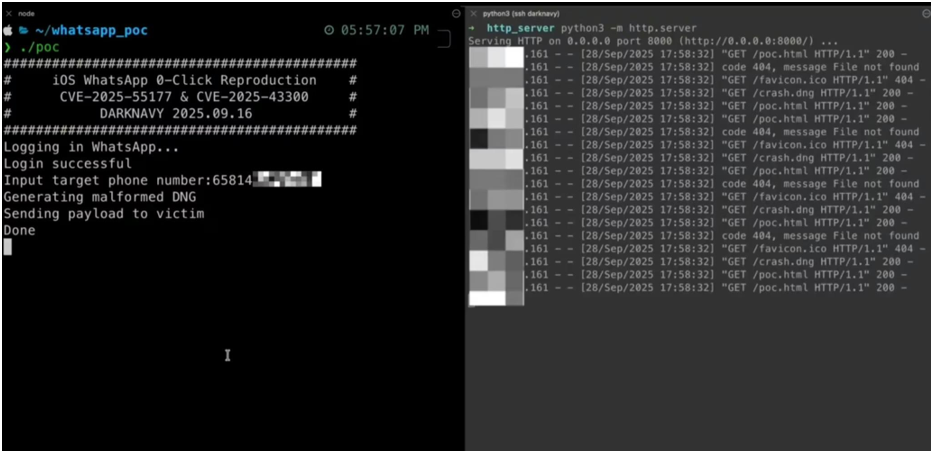
The exploit chain combines two distinct vulnerabilities (CVE-2025-55177 &CVE-2025-43300), enabling attackers to fully compromise a target device without user interaction.
This zero-click WhatsApp RCE vulnerability is a high-severity, cross-platform threat with potential for widespread exploitation.
Exploit Chain Breakdown
CVE-2025-55177 – Message Authentication Bypass
• Root Cause: Missing validation check in WhatsApp’s message handling logic.
• Impact: Allows attackers to send malicious messages disguised as originating from a trusted linked device.
• Result: Bypasses security controls, enabling initial payload delivery.
CVE-2025-43300 – DNG File Parsing Memory Corruption
• Root Cause: Flaw in WhatsApp’s DNG image parsing library.
• Impact: Processing a malformed DNG triggers memory corruption.
• Result: Enables remote code execution (RCE).
Risk & Impact
• Attack Surface: WhatsApp on iPhones, iPads and Mac computers
• Threat: Full device takeover (data theft, surveillance, malware deployment)
• Stealth: No visible indicators of compromise
• Likelihood of Exploitation: High (zero-click vectors are highly sought after in APT and cybercrime operations)
Mitigations
● Ensure WhatsApp and Apple OS platforms are patched to the latest versions once updates are released.
● Monitor for anomalous WhatsApp activity, unexpected image processing, or unexplained device behavior.
● Educate stakeholders that some attacks require no interaction and can evade traditional detection methods.
● Restrict or disable automatic media downloads to prevent automatic parsing of malicious files.
● Ensure devices receive security fixes promptly without relying on manual installs.
● Enforce app/OS versions, restrict unauthorized installs and centrally apply security configurations.
● Audit WhatsApp web usage and unlink unknown or unused sessions to reduce spoofing risks.
● Remove unnecessary access to microphone, camera, files and location to minimize compromise impact.
● Enforce strong passcodes and device encryption to protect stored data.
● Enable MFA for linked services to reduce fallout from stolen credentials or tokens.







.png)
.png)