Alleged Database Breach &Sale Detected of Nigerian-based data service platform
Source: Underground Hacker Forum
Classification: Confidential
Threat Level: Critical - Active Sale
Key Findings
· 65,000- Records Compromised
· 2025- Alleged Leak Date
· 10+ Data Categories
· Geographic Focus: Nigerian User Base with Multi-Bank Financial Data
· Distribution Method: Forum Private Messaging + Telegram
· Transaction Security: Escrow &Middleman Services Accepted
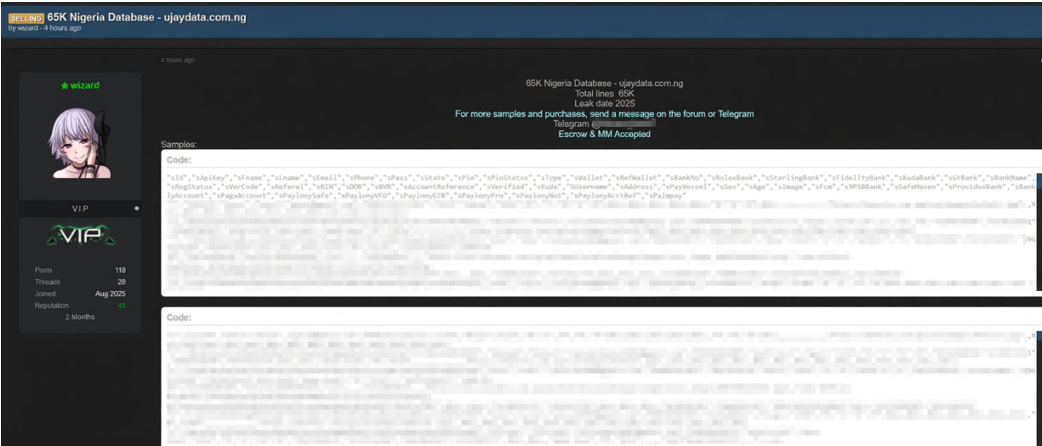
Breach Overview
A sophisticated threat actor has listed for sale an extensive database allegedly exfiltrated from a Nigerian-based data service platform. The dataset contains 65,000 user records encompassing highly sensitive personal identifiable information (PII) and critical financial credentials. The sale is being conducted through encrypted channels with professional monetization tactics including escrow services and Telegram-based transactions.
Compromised Data Categories
The following data types have been identified in sample records provided by the threat actor: User Ids, Full Names, Email Addresses, Phone Numbers, Passwords (Hashed/Cleartext), Physical Addresses, State/Pin Codes, Nin (National Id Numbers), Date Of Birth, BVN (Bank Verification Numbers), Bank Account Details, Financial Wallet Data. Multiple Nigerian banking and fintech platforms referenced in the compromised dataset.
Key Intelligence Insights
1. Extensive PII & Financial Data Exposure
The breach encompasses a comprehensive identity profile including National Identification Numbers (NIN),Bank Verification Numbers (BVN), cleartext or weakly hashed passwords, and direct financial account credentials across multiple banking institutions. This combination creates an optimal dataset for large-scale identity theft, account takeover attacks, and sophisticated financial fraud operations.
2. Unusual Future "Leak Date" Anomaly
The stated "Leak date2025" represents a critical temporal anomaly requiring immediate investigation. This designation could indicate: (A) an ongoing active compromise with anticipated future data exfiltration, (B) a pre-planned breach timeline suggesting insider threat activity, (C) misrepresentation or obfuscation by the threat actor, or (D) a persistent backdoor with continuous data harvesting capabilities. This anomaly demands urgent forensic analysis to determine the true breach timeline and assess whether unauthorized access remains active.
3. Targeted Nigerian User Base
The organizations’ domain and extensive Nigerian banking institution references indicate a concentrated targeting of Nigerian nationals. This geographic specificity increases vulnerability for affected individuals and creates concentrated risk for the Nigerian financial ecosystem, potentially enabling coordinated fraud campaigns against multiple institutions simultaneously.
4. Professional Monetization Infrastructure
The structured sale methodology utilizing established hacker forums, offering escrow protection, providing Telegram-based secure communications, and advertising professional middleman services demonstrates a mature cybercriminal operation. This professional approach indicates experienced threat actors with established dark web presence and suggests the data will be leveraged for maximum financial exploitation across multiple buyer networks.
Recommended Mitigation Strategies
· Urgent Data Breach Verification &Incident Response
This Nigerian-based data service platform must immediately verify the authenticity and full scope of this alleged breach through comprehensive log analysis and system auditing. Initiate formal incident response procedures including containment, eradication, and recovery phases. Execute immediate legal and regulatory notifications in compliance with Nigerian Data Protection Act(NDPA) and relevant financial sector requirements. Establish crisis communication protocols and engage external cybersecurity forensics specialists.
· Mandatory Password Reset & MFA Implementation
Force immediate password resets for all user accounts within the ujaydata.com.ng platform. Require strong, unique credential generation with minimum complexity requirements. Implement mandatory multi-factor authentication (MFA) across all user accounts to prevent credential stuffing and account takeover attacks. Deploy rate limiting and CAPTCHA mechanisms to prevent automated authentication abuse.
· User Notification & Financial Monitoring Guidance
Issue immediate transparent breach notifications to all potentially affected users with detailed guidance on protective actions. Advise users to monitor bank accounts, mobile wallet transactions, and credit reports for unauthorized activity. Provide access to identity theft protection resources and establish dedicated support channels.
· Enhanced Data Security & Access Controls
Conduct comprehensive security infrastructure audit focusing on database encryption at rest and in transit, access management protocols, vulnerability assessment and remediation, intrusion detection system deployment, and employee security awareness training. Implement database activity monitoring (DAM) to detect anomalous data access patterns. Review and harden API security, eliminate unnecessary data retention, and enforce strict principle of least privilege across all system access points.
· Threat Hunting & Persistent Access Elimination
Deploy threat hunting operations to identify potential backdoors, persistent access mechanisms, or ongoing data exfiltration activities. The anomalous "2025 leak date" suggests possible continuous compromise requiring thorough investigation of system logs, network traffic patterns, and unauthorized access attempts. Review all administrative accounts, service accounts, and third-party integrations for signs of compromise or abuse.

.jpeg)






.png)
.png)