CWE: CWE-288 Authentication Bypass Using an Alternate Path or Channel
Impact: Improper Access Control
Severity: Critical
A critical authentication bypass vulnerability has been identified affecting multiple Fortinet products (FortiOS, FortiManager & FortiAnalyzer) that support FortiCloud Single Sign-On for administrative access. Successful exploitation allows an attacker with a valid FortiCloud account and at least one registered device to authenticate to other Fortinet devices that are registered under different customer accounts, provided FortiCloud SSO is enabled on those devices.
This issue has been observed in active exploitation. Fortinet has taken containment actions at the FortiCloud service level and released fixed software versions. All customers using FortiCloud SSO for administrative access should treat this as a priority remediation.
The vulnerability resides in the FortiCloud SSO authentication workflow used for administrative logins. Improper validation of device-to-account association during SSO authentication allows a trusted FortiCloud identity to be accepted by devices that are not owned by the same FortiCloud account.
An attacker who controls a FortiCloud account and has at least one legitimate device registered can leverage this vulnerability to gain administrative access to other exposed devices where:
· FortiCloud SSO login is enabled
· The device is running a vulnerable firmware version
This does not require prior compromise of the target device itself. The weakness is purely in the authentication workflow enforced during the SSO exchange.
FortiCloud SSO administrative login is not enabled in factory default configurations. Exposure typically occurs during device registration when an administrator registers a device to FortiCare via the GUI, the option “Allow administrative login using FortiCloud SSO” is enabled by default unless manually disabled during registration. Devices onboarded in this manner may unknowingly expose an additional remote administrative authentication path.
Fortinet confirmed exploitation in the wild by at least two malicious FortiCloud accounts. These accounts were disabled on 22nd January 2026. Additional infrastructure associated with the activity were also detected and acted upon.
After gaining access through SSO, the threat actor’s primary objectives were:
· Downloading device configuration files
· Creating new local administrator accounts for persistent access
This indicates post-authentication objectives aligned with network reconnaissance, credential harvesting and long-term persistence establishment.
Affected Products and Fixed Versions
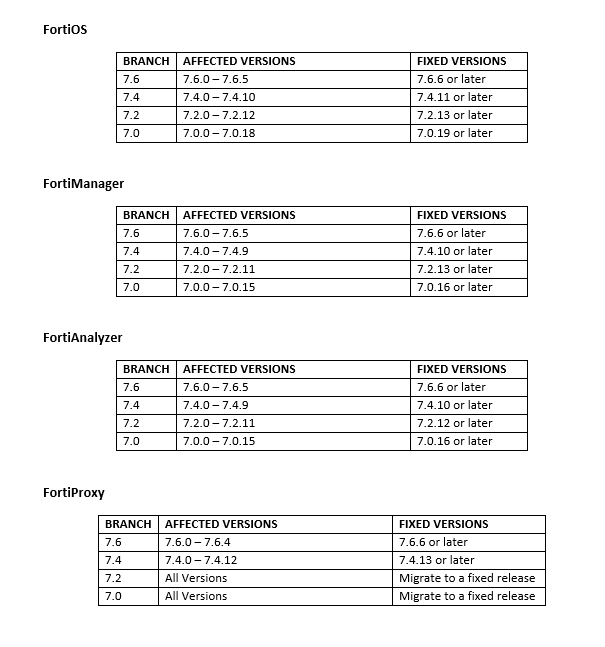
Under Investigation: FortiWeb, FortiSwitch Manager
Fortinet initially disabled the FortiCloud SSO but has now been re-enabled with enforcement that blocks authentication from vulnerable firmware versions. Devices that remain unpatched will not be able to use FortiCloud SSO until upgraded.
INDICATORS OF COMPROMISE
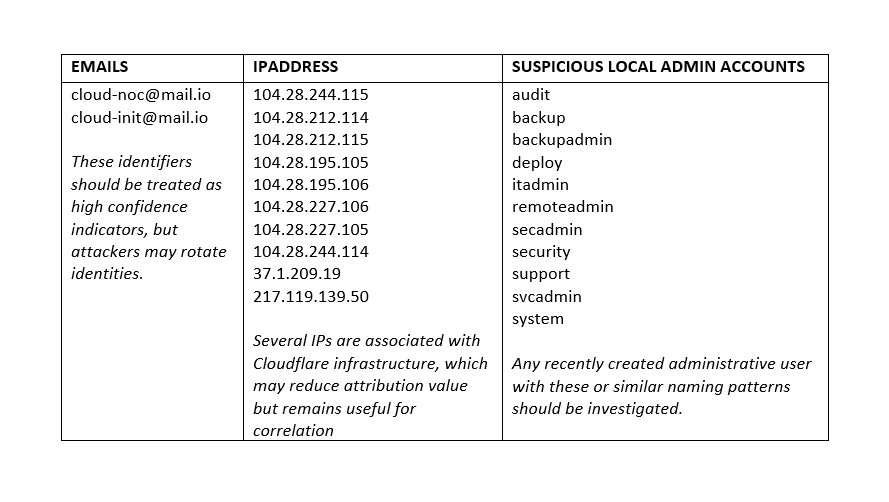
Detection Opportunities
- Successful admin logins via FortiCloud SSO outside normal maintenance windows
- Admin logins from unusual geographies or ASN ranges
- Creation of new super admin or admin related profile users
- Configuration backups initiated by unfamiliar accounts
- CLI command history showing account creation or privilege modification
The esentry team is actively on ground to follow up on any remedial actions and we will be constantly updating our customers








.png)
.png)