The attackers didn’t break the door; they simply handed victims a document and waited.
A newly uncovered campaign linked to the Russian state-aligned hacking group APT28 turns an ordinary Microsoft Office file into a silent entry point.
The campaign, dubbed Operation Neusploit, exploits a previously unknown vulnerability to slip past defenses and settle in before organizations even realize they’ve been visited.
A single Microsoft Word-style attachment, disguised as an ordinary RTF file, can quietly unlock a victim’s computer, steal emails, and install long-term surveillance tools all without triggering the alarms most organizations rely on.
Microsoft rushed out an emergency security update on January 26, 2026. Investigators still observed attackers actively exploiting systems days later suggesting some victims had already been compromised before the patch was applied.
The Trap Hidden Inside a Document
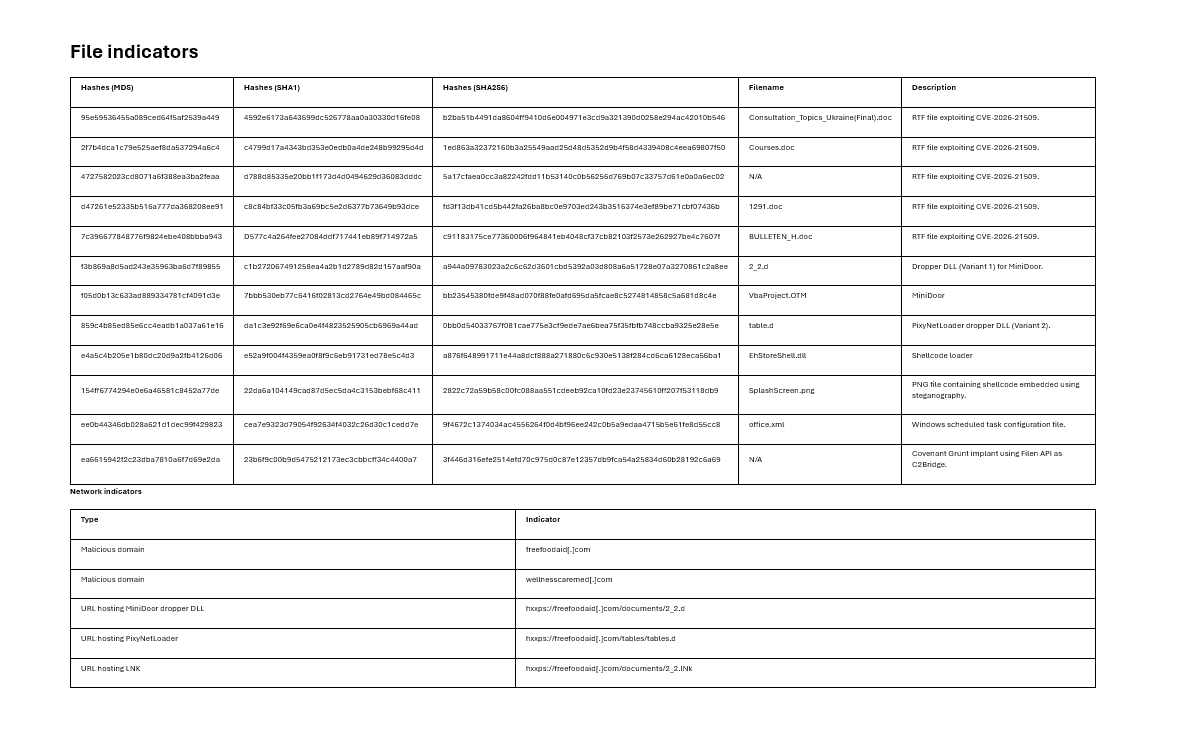
The attack exploits a critical vulnerability, CVE-2026-21509, in Microsoft Office.
The attackers prepared two different infection paths, giving them flexibility depending on the target.
When Your Email Client Starts Spying on You
In the first pathway, the attackers deploy a lightweight tool called MiniDoor, essentially turning Microsoft Outlook into a quiet informant.
The malware secretly lowers Outlook’s security settings, enables hidden macros, and begins scanning inboxes, junk folders and drafts. Emails are then forwarded to attacker-controlled accounts, while the software cleverly erases traces, so victims never see copies in their sent mail.
MiniDoor resembles a previous espionage tool linked to APT28, suggesting the group is refining its tradecraft.
A More Elaborate Break-In
The second pathway is more complex and far stealthier.
A loader known as PixyNetLoader buries malicious code inside what appears to be an ordinary image file. The computer later extracts hidden instructions from the picture using steganography, a technique often compared to hiding a message ininvisible ink.
From there, the system installs a remote-control implant based on the open-source Covenant framework. Instead of contacting suspicious hacker servers directly, it communicates through legitimate cloud storage infrastructure, blending into everyday internet traffic like a whisper in a crowded room.
The campaign is attributed to APT28 based on targeting patterns, reused malware components, and infrastructure tactics seen in previous operations. The attackers even restricted downloads to specific geographic regions, making the malicious files harder for outsiders to obtain and analyze.
MITIGATIONS
· Deploy Microsoft’s security update addressing CVE-2026-21509 across all Office installations and verify update compliance, including remote and offline systems.
· Restrict or sandbox RTF attachments from external sources and disable automatic loading of embedded objects in Office documents received via email or web downloads.
· Enforce “block all macros from the internet,” monitor for unauthorized VbaProject.OTM files, and alert on registry changes that weaken Outlook security settings.
· Monitor registry paths associated with the Enhanced Storage Shell Extension and investigate unexpected scheduled tasks (e.g., suspicious tasks restarting explorer.exe).
· Alert on Office spawning command interpreters, DLL downloads after document opening, in-memory .NETexecution, and suspicious process injection activity
· Monitor and control connections to file-sharing APIs and investigate unusual encrypted outbound traffic from Office or Explorer processes.








.png)
.png)