PDFSIDER is a sophisticated backdoor malware family engineered to evade modern endpoint detection and response (EDR) solutions through DLL sideloading, in-memory execution, and strongly encrypted command-and-control (C2)communications.
Threat actors are actively distributing PDFSIDER via targeted spear-phishing campaigns masquerading as legitimate PDF software installers. The malware establishes persistent remote access while leaving minimal forensic artifacts, significantly complicating detection and response.
Attack Delivery
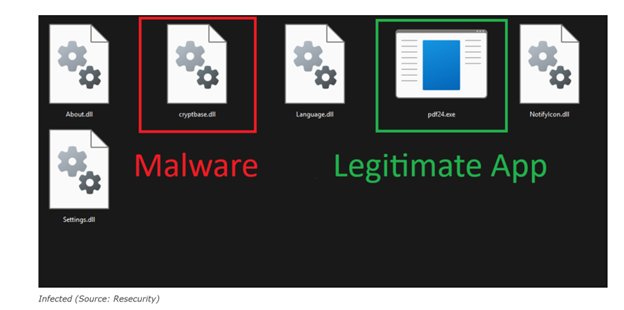
The PDFSIDER infection chain begins with spear-phishing emails delivering ZIP archives containing a trojanized executable impersonating the widely used PDF24 Creator application.
- The campaign abuses trust in PDF24 Creator (Miron Geek Software GmbH) as social engineering cover.
- The malicious executable (Pdf24.exe) is digitally signed, enabling it to bypass basic signature-based security controls.
- Upon execution, the application appears inactive to the user while malicious activity initiates silently in the background.
This delivery method capitalizes on user trust and routine software installation behaviour, making it highly effective in enterprise environments.
DLL Side-Loading Abuse
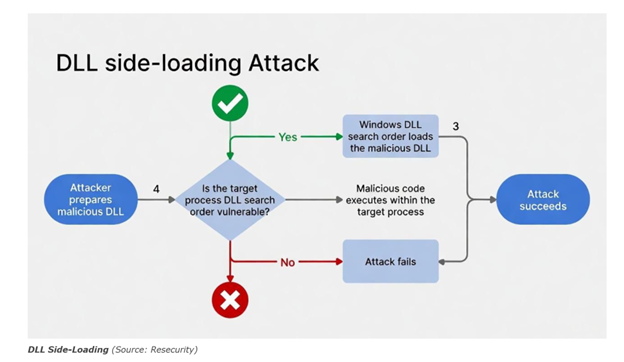
PDFSIDER achieves execution through DLL side-loading, a technique that exploits Windows’ default DLL search order:
- A malicious cryptbase.dll is placed in the same directory as the legitimate Pdf24.exe.
- During execution, the application loads the attacker-controlled DLL instead of the legitimate system library.
- This results in arbitrary code execution under the context of a trusted, signed binary.
Because the parent process is legitimate and signed, behavioural detection is significantly degraded, allowing the malware to blend into normal system activity.
Post-Execution Behaviour
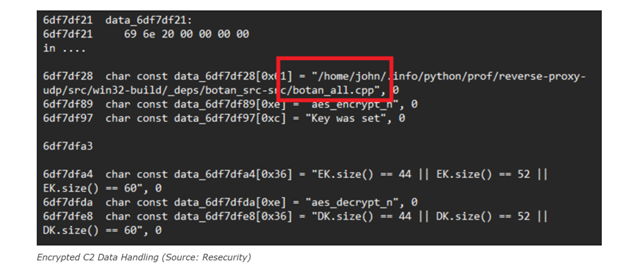
Once loaded, PDFSIDER establishes a covert C2 channel using the Botan 3.0.0cryptographic library, implementing:
- AES-256-GCM encryption
- Authenticated Encryption with Associated Data (AEAD)
All command execution and data exfiltration traffic is fully encrypted, protecting both payload confidentiality and integrity.
Key behaviours include:
- Initialization of Winsock APIs for direct network communication
- Collection of host reconnaissance data (username, hostname, process identifiers)
- Execution of attacker commands via hidden cmd.exe processes using the CREATE_NO_WINDOW flag
- Predominantly memory-resident operation, minimizing disk-based indicators
This operational profile is consistent with advanced espionage-oriented tradecraft, rather than opportunistic or financially motivated malware.
Evasion Techniques
PDFSIDER incorporates multiple safeguards to evade dynamic analysis and sandbox execution:
- Environment validation
- Uses Global Memory Status Ex to check available RAM
- .Terminates execution on low-memory systems commonly associated with sandboxes
- Debugger detection
- Leverages Is Debugger Present to prevent execution under analysis tools
These controls significantly reduce visibility during malware detonation and hinder reverse engineering efforts.
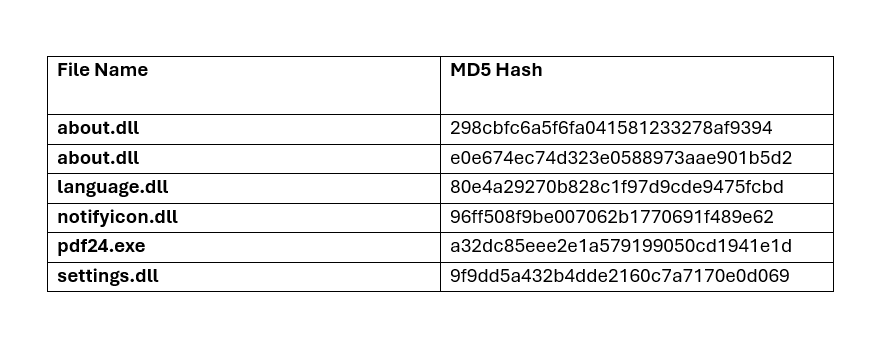
Indicators of Compromise (IOCs)
Recommendations:
Restrict execution of unsigned or unexpected executables claiming to be software updates.
Enforce heightened scrutiny of email-delivered ZIP archives and installer files.
Configure EDR solutions to:
· Detect DLL side-loading behaviour
· Alert on non-system cryptbase.dll loads
Monitor DNS and outbound encrypted traffic (including port 53 abuse) for anomalous C2 patterns.
Apply applications allow-listing for high-risk software categories such as PDF utilities.







.png)
.png)