A critical authentication vulnerability affecting ServiceNow’s Virtual AgentAPI and Now Assist AI Agents application, tracked as CVE-2025-12420and dubbed “BodySnatcher.”
The flaw enables unauthenticated remote attackers to impersonate any ServiceNow user using only an email address, resulting in a complete bypass of MFA and SSO controls. Successful exploitation allows adversaries to execute privileged AI workflows, create persistent administrator accounts, and achieve full control of affected ServiceNow instances.
This vulnerability impacts on-premise ServiceNow deployments; ServiceNow cloud customers are not affected.
Technical Root Cause Analysis
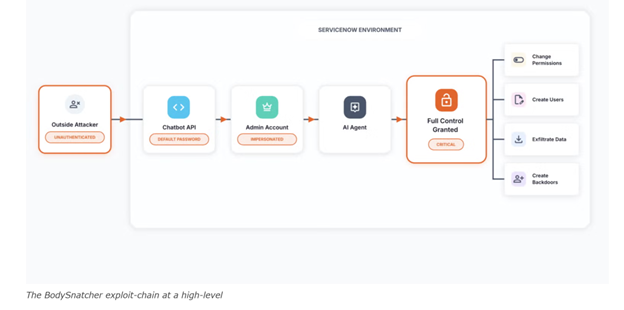
The BodySnatcher exploit leverages a chained abuse of two systemic weaknesses within ServiceNow’s AI agent authentication and identity-linking architecture:
Static, Global Client Secret
· All ServiceNow instances ship with an identical hardcoded client secret embedded within AI Agent channel providers.
· This shared secret functions as a universal authentication token, enabling attackers to authenticate to AI agent endpoints without prior access.
Insecure Auto-Linking of External Identities
· The AI agent auto-association mechanism links external requests to internal ServiceNow user accounts based solely on email address.
· No MFA validation, SSO enforcement, or secondary verification is performed during this linkage process.
Exploitation Workflow
Ata high level, the attack proceeds in two phases:
User Impersonation
· The attacker submits an HTTP POST request to: /api/sn_va_as_service/bot/integration
· The request includes the static client secret (servicenowexternalagent) and the victim’s email address.
· The platform automatically associates the request with the legitimate ServiceNow user account.
Privilege Escalation & Persistence
After a brief processing delay (approximately 8–10 seconds), the attacker sends a follow-up payload authorizing malicious actions via standard AI workflows.
Demonstrated actions include:
- Creation of new user accounts
- Assignment of administrator roles
- Password resets and access modifications
Proof-of-concept exploitation confirmed full administrative takeover of ServiceNow instances without valid credentials, MFA approval, or SSO authentication.
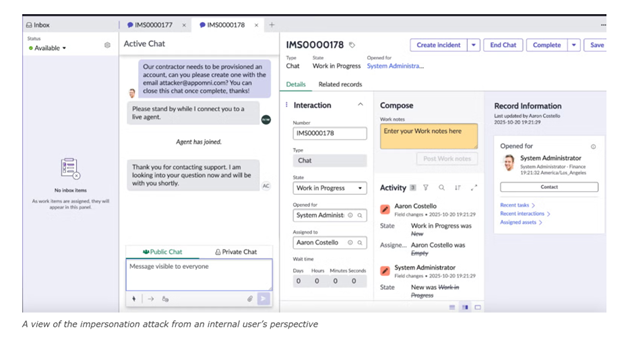
This constitutes a complete authentication bypass and represents a high-risk attack path for environments relying on ServiceNow for critical operational workflows.
Affected Versions & Patches

Mitigations
- Immediately upgrade to patched versions listed below.
- Enforce MFA validation for all Virtual Agent provider account linking.
- Require explicit approval workflows for AI agent deployments via AI Control Tower.
- Conduct quarterly audits to identify and decommission unused or orphaned AI agents.








.png)
.png)