What if the malware attacking your system never dropped a real file, never raised an alert, and never asked for admin rights?
That’s exactly how this newly discovered Pulsar RAT campaign operates abusing trusted Windows utilities, executing payloads in memory, and maintaining long-term access while staying almost completely invisible to traditional defenses.
The malware is engineered to maintain long-term persistence while minimizing its forensic footprint and bypassing conventional detection mechanisms.
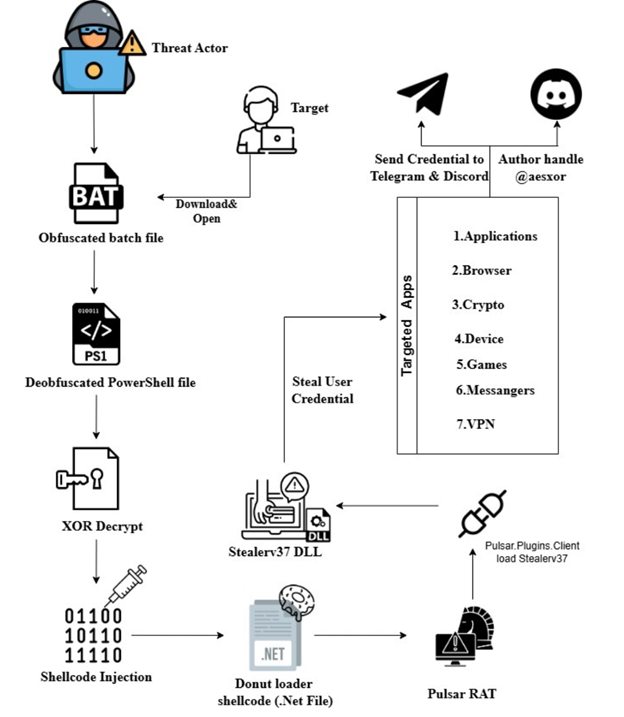
Initial Access & Persistence
The infection chain begins with a concealed batch file that establishes persistence via the per-user Run registry key:
HKCU\Software\Microsoft\Windows\CurrentVersion\Run
To avoid detection during routine inspection, the malware creates a hidden directory within %APPDATA%\Microsoft\, using randomized naming conventions. The batch file registers itself under a benign-looking value name, ensuring execution at every user logon without requiring elevated privileges.
This persistence stub copies itself into the hidden directory and incorporates aretry loop to guarantee execution continuity across system reboots.
Payload Delivery & Execution
The batch file extracts an embedded Base64-encoded payload demarcated by a predefined delimiter. This payload is decoded into a PowerShell script andwritten to the %TEMP% directory. Execution occurs with the PowerShell execution policy bypassed, and the script implements self-deletion routines to reduceforensic artifacts.
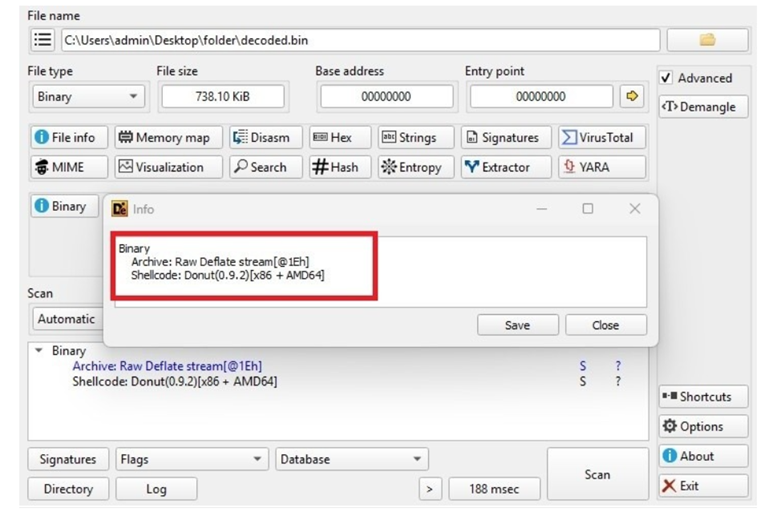
The decoded PowerShell script contains a large byte array that undergoes XORdecryption, revealing Donut-generated shellcode designed forposition-independent execution.
The loader performs classic process injection using Win32 APIs such asOpenProcess, VirtualAllocEx, WriteProcessMemory, and CreateRemoteThread. After an intentional 80-second delay likely to evade behavioral analysis, the shell code is injected into memory using PAGE_EXECUTE_READWRITE permissions.
To maintain resilience, the malware includes a watchdog mechanism that monitors the injected process and automatically migrates to explorer.exe if the host process terminates.
Anti-Analysis & Evasion
The decrypted payload exposes a heavily obfuscated .NET assembly implementing extensive anti-analysis defenses. These include virtualization, sandbox, andemulation detection routines designed to thwart automated analysis environments.
A dedicated background thread continuously scans for debugging activity,suspicious memory regions, injected threads, and both managed and native debuggers. Upon detection of tampering, execution is immediately terminated.
User-mode anti-debugging techniques are also employed, including window enumeration todetect reverse-engineering tools such as x64dbg, WinDbg, dnSpy, and IDA.
Reconnaissance & Data Theft
PulsarRAT’s modular stealer component targets a wide range of applications, including:
- Remote access tools: AnyDesk, TeamViewer, PuTTY
- FTP clients: FileZilla, WinSCP
- VPN software: NordVPN, ExpressVPN
- Messaging platforms: Discord, Telegram
- Developer tools: GitHub, JetBrains IDEs
Browser data harvesting includes credentials, cookies, autofill entries, stored creditcards, and authentication tokens across multiple profiles.
During analysis, execution of the XOR decryption routine results in a decoded.binfile, which is subsequently examined to determine its underlying file type.
Command & Control
The malware supports real-time surveillance features, including clipboardmonitoring for cryptocurrency addresses, webcam access with frame capture, andcontinuous audio recording via Windows Core Audio APIs.
Exfiltration is conducted through Discord webhooks and Telegram Bot APIendpoints, using multipart POST requests that include victim metadata such asusername, hostname, OS version, and malware build identifier.
Remote system-control capabilities allow attackers to enable or disable Task Managerand User Account Control (UAC), significantly limiting user intervention.
Stolen data is consolidated into ZIP archives containing a detailed summary filelabeled “InteliX by dead artis”, attributed to the threat actor @aesxor.
MITIGATIONS
· Prioritize detection of in-memory execution, process injection, abnormal API call chains, and long execution delays. Signature-based AV alone will not catch fileless malware.
· Enforce PowerShell Constrained Language Mode, disable PowerShell v2, and enable ScriptBlock Logging. Actively monitor script execution from user-writable locations such as %TEMP% and %APPDATA%.
· Continuously monitor the HKCU\Software\Microsoft\Windows\CurrentVersion\Run registry key and alert on benign-looking entries pointing to hidden or randomized user directories.
· Enable Attack Surface Reduction rules to prevent process injection and suspicious parent-child relationships, particularly scripts or command shells injecting into explorer.exe.
· Enforce outbound traffic controls and monitor for unauthorized use of legitimate services such as Discord web hooks and Telegram Bot APIs, especially following reconnaissance or credential access activity.







.png)
.png)