Email might be the lifeblood of business, but it’s also the playground of APT groups who apparently wake up every morning and choose violence.
Just like ToddyCat, the APT crew that refuses to touch grass and instead keeps leveling up like it’s a cyber-RPG.
At first glance you’d think cloud email(Microsoft 365, Gmail) means “safer.”
But toddy cat would make you have second thoughts, as they have evolved from simple credential theft to full-on browser looting → OST file heisting → token hunting to quietly siphon corporate emails.
Toddy Cat’s old toolkit (C# / C++) was already an annoying credential-harvesting menace. But by late 2024–2025, they debuted a PowerShell edition, because why not weaponize admins' favorite scripting language too?
What the PowerShell version does:
- Runs with domain controller privileges .
- SMB walks every host listed in uhosts.txt.
- Copies Chrome/Edge Login Data, Cookies, Local State, History.
- Pulls Firefox credentials and profile folders too.
- Collects DPAPI master keys so they can decrypt everything later offline.
- Stores everything neatly in c:\programdata\temp\.
SMB-based scraping = low noise, blends into normal Windows admin traffic, and is annoying to detect.
Toddy Cat’s Offline Email Buffet
When monitoring tools started catching browser scraping, ToddyCat switched strategies:
“Fine. We’ll just steal Outlook OSTs directly.”
OST files = offline copies of entire mailboxes.
The tool used:
- A 32-bit C++ binary
- Takes <source> and <destination> paths
- Reads sectors directly using raw disk handles
- Steals OST → saves as .ost2 → attacker extracts emails using XstReader
Sharp Token Finder + ProcDump Rebrand
Since grabbing files on monitored hosts causes alarms, ToddyCat tried something more elegant:
steal Microsoft 365 access tokens from memory.
Use Sharp Token Finder
- Searches memory dumps of Outlook, Teams, OneDrive, Word, SharePoint, etc.
- Dumps processes → scans for JWT tokens using pattern: eyJ0eX [a-zA-Z0-9. _-]+
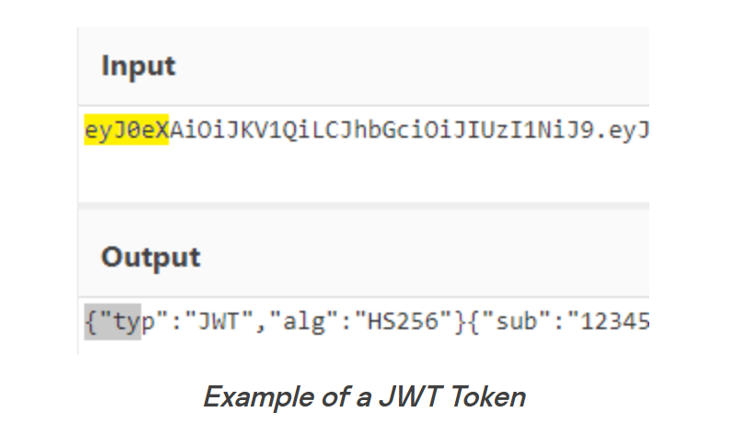
Didn’t EPP block it?
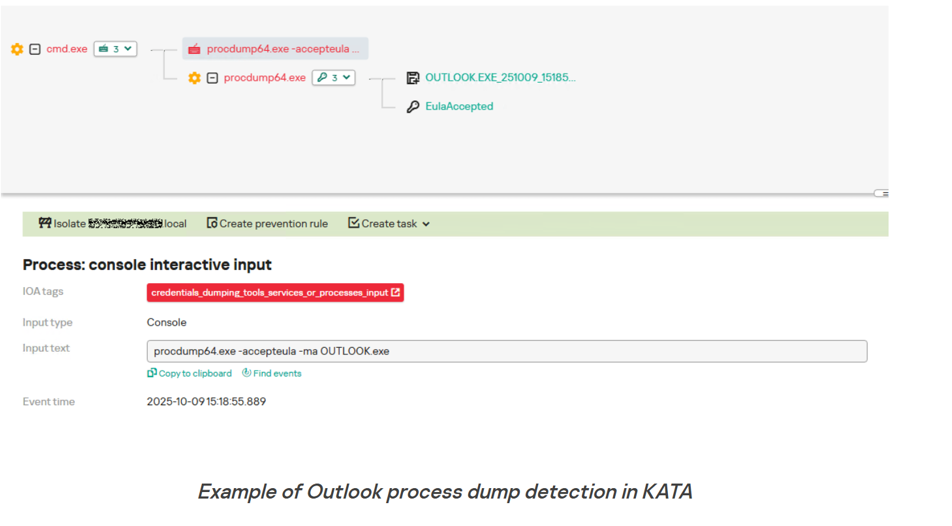
Yes it did, but they just switched to ProcDump:
procdump64.exe -accepteula -maOUTLOOK.exe
rar.exe a -m5 dmp.rarOUTLOOK.EXE_<id>.dmp
Then: exfil → parse tokens → login →steal mailbox → disappear.
ToddyCat is adapting fast:
- If you block browser theft → they move to raw disk reads
- If you block disk reads → they dump tokens
- If you block token dumps → they probably start astral projecting into Azure AD next
Almost everything they do is detectable, but only if you're looking at the right places.
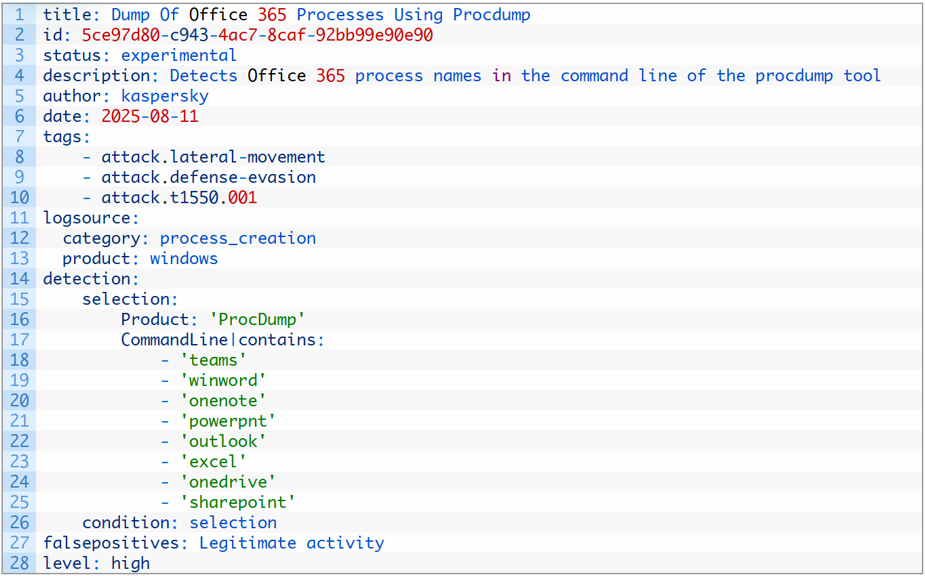
Detection
To detect this technique, it’s necessary to monitor the ProcDump process command line for names belonging to Microsoft 365application processes.
Indicators of compromise
Malicious files
55092E1DEA3834ABDE5367D79E50079A ip445.ps1
2320377D4F68081DA7F39F9AF83F04A2 xCopy.exe
B9FDAD18186F363C3665A6F54D51D3A0 stf.exe
Not-a-virus files
49584BD915DD322C3D84F2794BB3B950 XstExport.exe
File paths
C:\programdata\ip445.ps1
C:\Windows\Temp\xCopy.exe
C:\Windows\Temp\XstExport.exe
c:\windows\temp\stf.exe
PDB
O:\Projects\Penetration\Tools\SectorCopy\Release\SectorCopy.pdb
Recommendations:
Use EPP/EDR+ network detection (KATA-level or equivalent).
Audit for:
- SMB access to browser credential paths
- DPAPI Master Key folder access
- Raw Access Read via Sysmon
- ProcDump targeting Office processes
Enforce conditional access + short token lifetimes in M365
Monitor anomaly logins to Exchange Online

.jpeg)






.png)
.png)