They say, “when the shepherd sleeps, the wolves roam free.” The shepherd is often our patching process, and this summer, while many organizationsare basking in the post-Patch Tuesday glow, a new breed of predator quietly slips through the fog.
The culprit is a new ransomware strain weaving its way through a chain of Microsoft SharePoint vulnerabilities. But this isn’t your average smash-and-grab job, this is ToolShell, a strategic, sophisticated campaign that has quietly breached at least 148 organizations worldwide, including some of the globe’s most high-stakes government and corporate networks.
Go Big or Go Home
The malware behind the mayhem is an evolved species, 4L4MD4R, a ransomware variant built on open-source Mauri870 code. Written in GoLang, the payload is UPX-packed to stay slim and sneaky.
The moment it lands, it decrypts an AES payload in-memory, allocates space, and spins up a new thread, this cookie deletes your files, encrypts your systems, and demands a sweet 0.005 Bitcoin ransom.
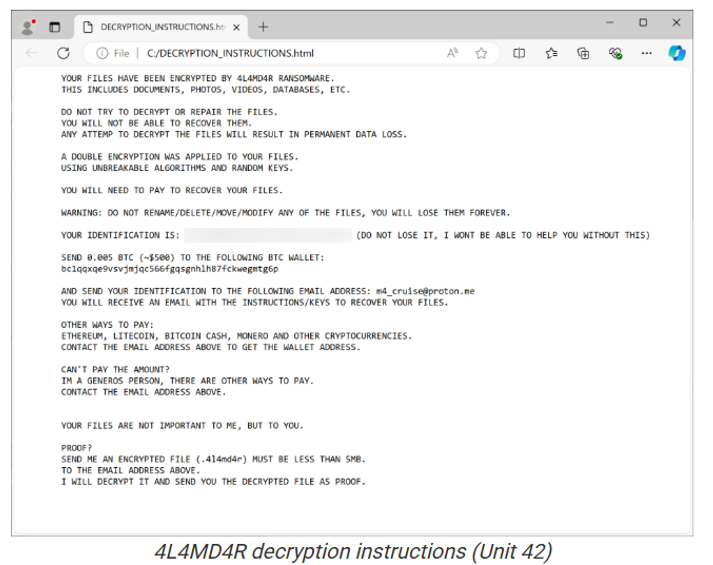
Microsoft has linked this campaign to three state-backed Chinese threat groups
- Linen Typhoon
- Violet Typhoon
- Storm-2603
Each has been observed exploiting the Tool Shell vulnerability chain with surgical precision.
This isn’t just one ransomware gang freelancing from a basement. This is nation-state-level recon, lateral movement, and timed detonation with SharePoint servers as the primary attack surface.
The Flaws That Opened the Flood gates
The campaign initially exploited CVE-2025-49706 and CVE-2025-49704 — zero-day vulnerabilities that let attackers waltz into SharePoint environment sun detected.
Microsoft, in a rare move, patched both bugs and reassigned them as:
- CVE-2025-53770 (now flagged by CISA as actively exploited)
- CVE-2025-53771
But here’s the kicker: even fully patched servers were compromised, thanks to additional chained logic flaws. This is an evolved threat actor. They aren’t just going for low-hanging fruit, they’re building the ladder.
Not Just a Numbers Game
Among the 148 confirmed breached entities are:
- The U.S. National Nuclear Security Administration
- Department of Education
- Florida’s Department of Revenue
- The Rhode Island General Assembly
- Multiple European and Middle Eastern government networks
According to Dutch security firm Eye Security, over 400 servers across multinational corporations and critical infrastructure are now serving as the attackers’ playground.
It’s not a campaign. It’s a siege.
How to Protect Your Organization
· Apply Microsoft’s July 2025 patches
· Scan for the following Indicators of Compromise (IOCs):
Domain: the innovation factory[.]it
IP: 145.239.97[.]206
Power Shell logs that modify ordisable Defender/Security Center
· Isolate internet-facing SharePoint servers and verify logs for unapproved access.
· Proactively hunt for UPX-packed GoLang binaries in your environment.
· Look for AES decryption patterns in memory and thread injection behaviors.
· Enable memory forensics on critical systems.
· Implement egress filtering to prevent connections to suspicious IPs/domains.
· Use application whitelisting to block rogue PowerShell executions.
· Shift to Zero Trust architecture for collaboration tools like SharePoint, segment what you can.
Remember to always patch it like your enemies are already in. Monitor like you're being watched.
Cause wolves never knock; they find an open gate!!








.png)
.png)