As organizations settle into the new year, threat actors are wasting no time exploiting familiar gaps. One of the earliest patterns emerging in 2026 is not a zero-day or a novel exploit, but the quiet reuse of stolen credentials to walk straight into corporate cloud environments.
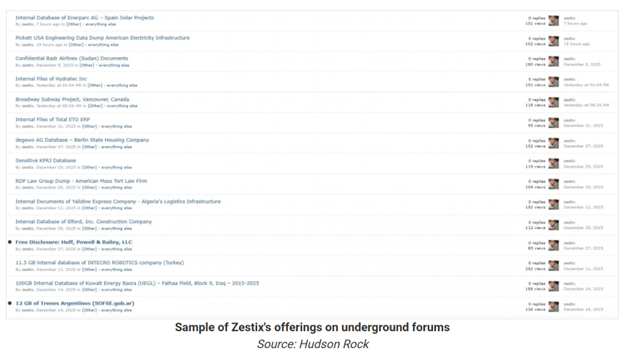
A threat actor operating under the name Zestix is currently advertising stolen corporate data from dozens of organizations, reportedly obtained after accessing ShareFile, Nextcloud, and own Cloud instances.
How Access Was Gained
Initial access was achieved using credentials collected by infostealers such as RedLine, Lumma, and Vidar, deployed on employee endpoints.
These malware families are typically spread via:
- Malvertising campaigns
- Fake software updates and ClickFix-style lures
Once installed, they quietly extract:
- Browser-stored credentials
- Autofill data and personal identifiers
- Messaging app sessions
- Crypto wallet information
Stolen usernames and passwords belonging to cloud file-sharing services without MFA enabled, allow attackers log indirectly, no exploit required.
Old Credentials, Active Sessions
One of the more concerning findings is not how the data was stolen, but how long access remained viable. Some of the credentials used by Zestix have existed in underground databases for years, suggesting that:
- Passwords were never rotated
- Active sessions were not invalidated
- Compromises went undetected long after initial infection
This points to a recurring defensive blindspot: endpoint compromise is treated as a local issue, while cloud access persists indefinitely.
Initial Access Broker in Action
Zestix appears to operate primarily as an Initial Access Broker (IAB), monetizing access to high-value corporate cloud environments rather than running ransomware directly.
After parsing infostealer logs for corporate cloud URLs, the actor logs into ShareFile or Nextcloud environments using valid credentials where MFA is absent, then exfiltrates data for resale.
What’s Being Sold
Zestix claims access to datasets ranging from tens of gigabytes to multiple terabytes, including:
- Aircraft maintenance manuals and fleet data
- Defense engineering files
- Customer records
- Mass-transit schematics
- Utility LiDAR maps
- ISP network configurations
- Satellite project documentation
- ERP source code
- Government contracts and legal records
Exposure at this level introduces not only privacy and regulatory risk, but also industrial espionage and national security implications.
While specific companies have not publicly confirmed breaches, it is important for us to emphasize that this is not an isolated campaign. Their broader telemetry shows thousands of infected machines, including systems associated with major enterprises such as Deloitte, KPMG, Samsung, Honeywell, and Walmart.
Remember, Cloud platforms are only as secure as the endpoints and identity controls protecting them.
In 2026, “we didn’t see any alerts” is no longer a defense, it’s a warning sign!!!!!







.png)
.png)