One Thing about wild kids is they would always pop in to say hello unannounced,
I know you are probably thinking, “Didn’t we just start the year?”
Yes, we did, but over on the threat block the day never ends and the night never comes
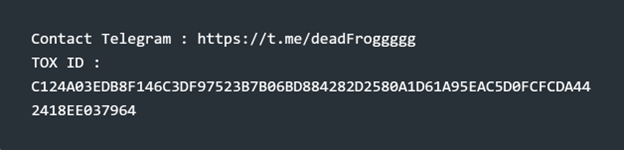
An underground tool from the arsenal of a newcomer wild kid, branded DeadFrog’s AV/EDR Killer, has surfaced on Breach Forums. advertised for $550.

The tool is promoted via Telegram and TOX and claims to disable a wide range of endpoint security solutions.
The campaign demonstrates the continued evolution of BYOVD (Bring Your Own Vulnerable Driver) techniques, enabling attackers to terminate “Protected Process Light” (PPL) services that normally resist administrative tampering.
Key Things Observed:
· Advertised on Breach Forums, with direct contact via Telegram and TOX.
· BYOVD loading a vulnerable driver to gain kernel-level privileges.
· Tool runs as NeaClean.exe, with Process Hacker showing “Service Created” before protected processes vanish.
· Instant termination of AV/EDR services across multiple vendors, leaving endpoints blind.
Demonstrated kills against major products including:
· SentinelOne
· MDE
· Sophos XDR
· ESET Endpoint Security
· TrendMicro
· Avast Business
· Avira Pro
· AVG
· Malwarebytes
· McAfee
· Panda Dome
· Sophos Home
· WebRoot
· Total defense
· Manage Defense
· TotalAV
· K7 Total
· PC Matic
· ZoneAlarm
· BullGuard
· Comodo
· QuickHeal
And More...
Possible Vendor Impact
· Avast Business: AvastSvc.exe terminated instantly, disabling scanning and firewall.
· Avira Pro: avguard.exe and Avira.ServiceHost.exe killed, removing real-time protection.
· Microsoft Defender (MDE): MsMpEng.exe killed notable given Defender’s kernel integration.
· ESET: ekrn.exe (core kernel service) terminated, UI frozen.
· Sophos: Tamper-protected services bypassed, entire process tree terminated.
· Trend Micro: Core services unloaded from memory, agent disabled.
DeadFrog’s tool highlights a dangerous trend: commercialized AV/EDR bypass kits lowering the barrier for adversaries. With kernel-level exploits packaged for sale, attackers can neutralize enterprise defenses before deploying ransomware, data theft, or persistence mechanisms.
Recommendations
- Driver Control: Enforce strict kernel driver policies and monitor for vulnerable driver loads.
- Detection: Watch for “Service Created” events and sudden AV/EDR process drops.
- Defense in Depth: Assume endpoint protection can be bypassed; layer detection and response.
- Threat Intel Monitoring: Track underground tool sales as early indicators of upcoming campaigns.
DeadFrog’s AV/EDR Killer is a stark reminder: attackers don’t just evade defenses, they erase them.
Stay Resilient!!!







.png)
.png)