As we step into a new year, threat actors are doing exactly what they have always done which is starting strong. While many organizations are setting resolutions around growth and resilience, attackers are beginning 2026 with something far more valuable: Data.
An unsecured MongoDB instance containing 16 terabytes of data was uncovered. The database was left wide open, exposing 4.3 billion professional records, a huge treasure box of Personally Identifiable Information (PII) ripe for exploitation.
The database was secured shortly after disclosure, but the critical question remains: who accessed it before the lock went on?
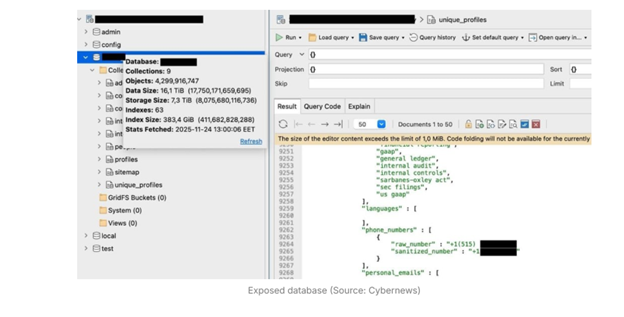
What Was Exposed
The dataset was clean, structured, and clearly built for scale. Researchers identified nine collections, several of which contained hundreds of millions to billions of records.
The exposed data included:
- Full names
- Email addresses
- Phone numbers
- Job titles and employment history
- Education records
- LinkedIn and other professional profile links
- Profile photos (over 700 million records)
Data Breakdown
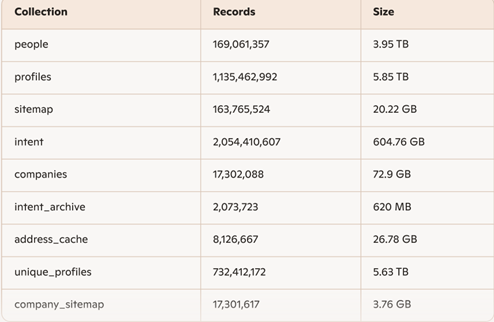
Three collections alone accounted for nearly 2 billion records. One collection, unique_profiles, held 732million distinct profiles, many with images: ideal material for impersonation and social engineering.
Some records were linked to Apollo.io-style identifiers, suggesting overlap with lead-generation ecosystems. While attribution remains unconfirmed, the data strongly resembles large-scale scraped and aggregated professional datasets, potentially pulling from multiple sources and older breaches dating back to 2021.
Why This Matters
This is not just another “data leak” headline. This is pre-weaponized intelligence.
At this volume and level of detail, the dataset enables:
- Highly targeted phishing campaigns
- Convincing business email compromise (BEC) and CEO fraud
- Automated social engineering at scale
- Precise targeting of employees in high-value organizations
For attackers, this kind of dataset removes guesswork. It allows filtering by role, company, seniority, and industry, turning attacks from opportunistic to surgical.
As we enter a new year, these records don’t expire. They will likely resurface throughout 2026 in phishing kits, scam scripts, and underground databases.
Even if individual records are partially outdated, attackers only need enough accuracy to succeed.
Recommendations
- Treat unsolicited, personalized emails with increased skepticism
- Reduce publicly exposed professional data where possible
- Assume exposure: If your professional data exists online, it’s likely already in circulation.
- Harden authentication: Unique passwords + mandatory 2FA across all accounts.
- Patch aggressively: Keep systems updated to close exploitable gaps.
Stay vigilant! Stay alert! and remember the new year doesn’t mean a clean slate for your data.







.png)
.png)